FirstBlood-#823 — Reflected XSS using Referer header on /login.php
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-29, yashamin Level 2 reported:
I found that in /login.php Referer header's value was reflected in <a href='REFLECTION_HERE'>. Here reflection is inside single quotes, so we can use single quote in the path of previous page to break the attribute's value. For example previous page's url should be https://example.com/'__other_attributes__
Also we won't be able to use chars like <, ", and [SPACE] because they will be url encoded referrer header's value will be reflected. To separate multiple attributes we can use slash, like for path /attr1='val1'/attr2='val2', reflected value will be <a href='http://example.com/'/attr1='val1'/attr2='val2'>.
To make the payload work without user interaction, I checked CSS files included in the page to find if there is any animation defined. In the /slider-revolution/revolution/css/settings.css file, I found that there was an animation named rev-ani-mouse. So the payload should have that animation and onanimationend event handler defined, which will be called when the animation ends.
POC
- Open https://webhook.site/
- Click on the edit button at top right corner, and change Content-Type to 'text/html' and change body to
<body>
<a
href="https://df7e3a3a0fe0-yashamin.a.firstbloodhackers.com/login.php"
referrerpolicy="unsafe-url"
>
click me
</a>
</body>
 You'll need to provide
You'll need to provide referrerpolicy attribute to anchor tag, so it will send the entire URL in Referrer header. You can also use meta tags or Referrer-Policy response header to define referrer policy.
- After saving, you'll see a unique URL, you can provide xss payload in the url.
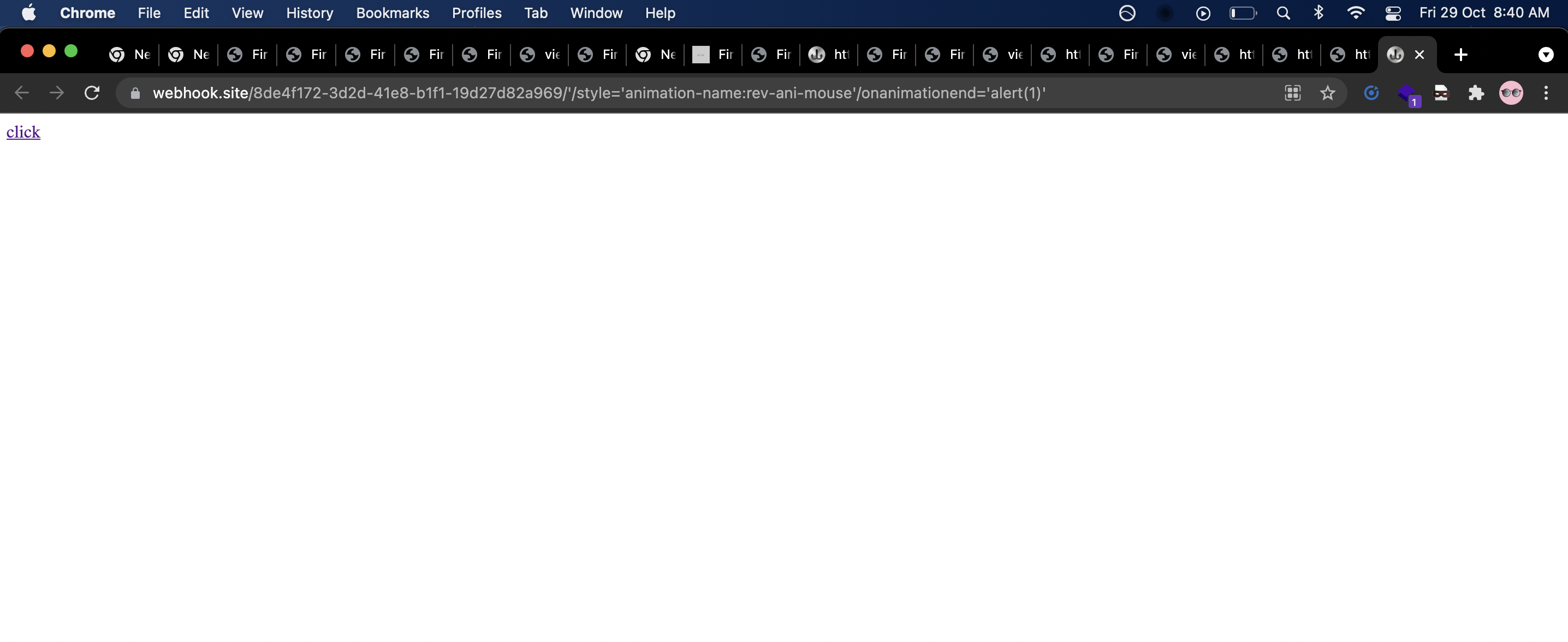
For my unique URL https://webhook.site/8de4f172-3d2d-41e8-b1f1-19d27d82a969, URL with the payload will be -
https://webhook.site/8de4f172-3d2d-41e8-b1f1-19d27d82a969/'/style='animation-name:rev-ani-mouse'/onanimationend='alert(1)'
- Open the above URL and click on the link, and you will see alert.


Impact
XSS can be used to execute JS code on victim's browser to perform read/write actions on their data.
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login.php
Parameter: Referer
Payload: '/style='animation-name:rev-ani-mouse'/onanimationend='alert(1)'
FirstBlood ID: 19
Vulnerability Type: Reflective XSS
The parameter ?ref= on login.php was fixed and instead the use of $_SERVER['HTTP_REFERER']; was used. Patrice tested in Chrome and Firefox and saw it was secure, but some users still use Internet Explorer 10 (governments for example!) and the Referer header is vulnerable to reflective XSS.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Nice find, thanks for providing a working PoC! Actually when testing this I was only able to reproduce on IE as it seems for me on latest versions of Chrome/FF the ' character was encoded, but perhaps I need to play around some more with this :D
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  You'll need to provide
You'll need to provide 


 Report Feedback
Report Feedback