FirstBlood-#833 — [BYPASS] Open URL Redirect on /drpanel/logout.php
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-29, buraaq Level 2 reported:
Hello zseano,
Summary
I have found a bypass to the Open redirect on /drpanel/logout.php?ref=.
Bypass filter
As we look at last hackevent's payload //https:\/\/www.google.com. Patrice has tried to filter two consecutive // to avoid OR but it can be bypassed easily by tab char %09, but the browser ignores it and joins them.
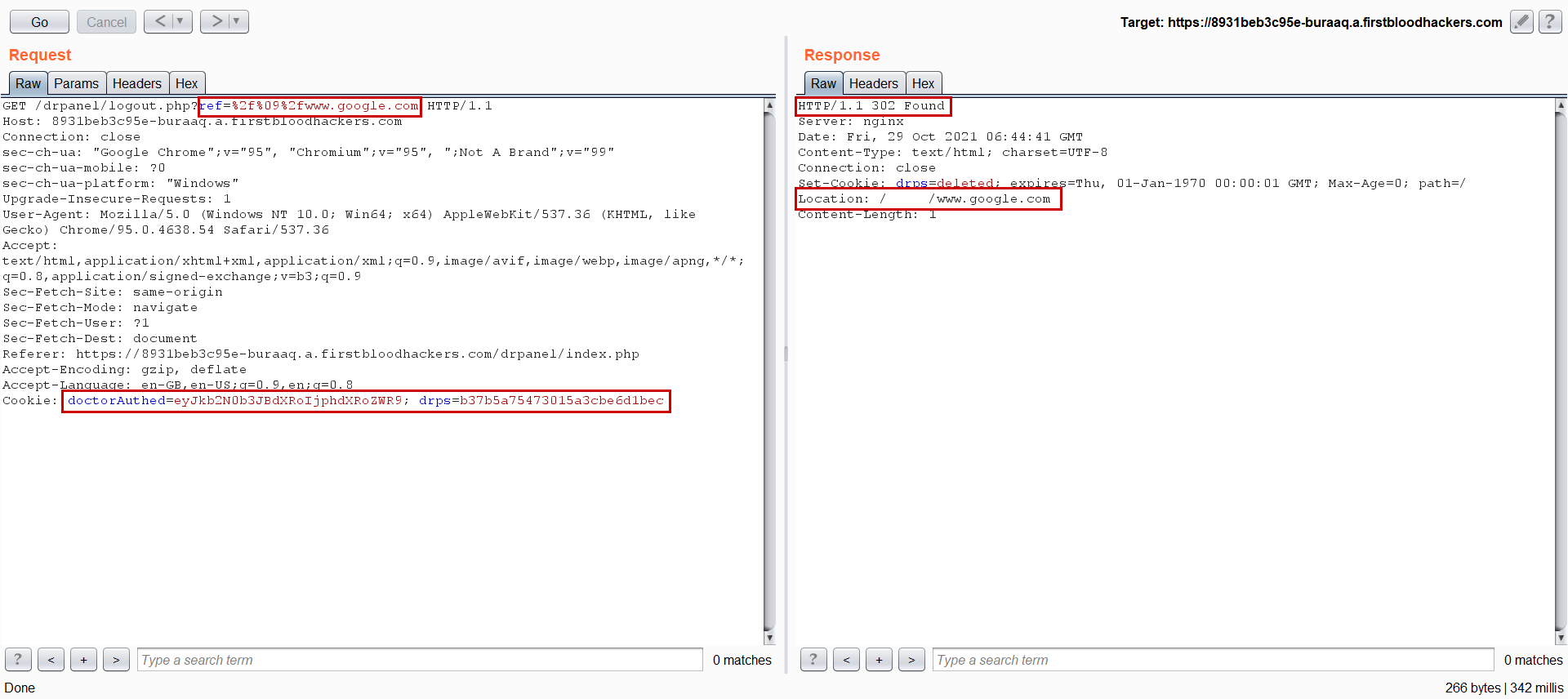
Payload "/%09/attacker.com" ---> / /attacker.com ---> //attacker.com
Steps to reproduce
- As a logged in Doctor, click on the securely sign out button to logout.
- Notice the endpoint has a ref variable.
- If you submit the following payload, the application will redirect the user to the
url provided by the payload: ref=%2f%09%2fattacker.com
POC
Impact
A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks.
Kind regards,
buraaqsec
This report has been publicly disclosed for everyone to view
P4 Low
Endpoint: /drpanel/logout.php
Parameter: ref
Payload: %2f%09%2fattacker.com
FirstBlood ID: 18
Vulnerability Type: Open Redirect
The open redirect bug on logout.php was fixed but the code still failed to filter out certain characters such as %09 and thus the endpoint is still vulnerable to open redirect. This vulnerability only affects chrome.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 