FirstBlood-#873 — Username enumeration and SQL Injection on Vaccine Management login page
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-29, sumyth Level 2 reported:
Hi,
Please find a brief description of the vulnerability below,
Summary
On firstbloodhackers.com, using directory fuzzing it is possible to identify vaccine management login page. The login page can further be bypassed by using username enumeration and finally using SQL Injection.
Steps to Reproduce:
-
Visit the login page at - https://9eebe8cbfef2-sumyth.a.firstbloodhackers.com/vaccination-manager/login.php
-
Input any random username into the form and observe that the server responds back with 'User does not exist' message. It is possible to utilize this behavior to enumerate a valid user.
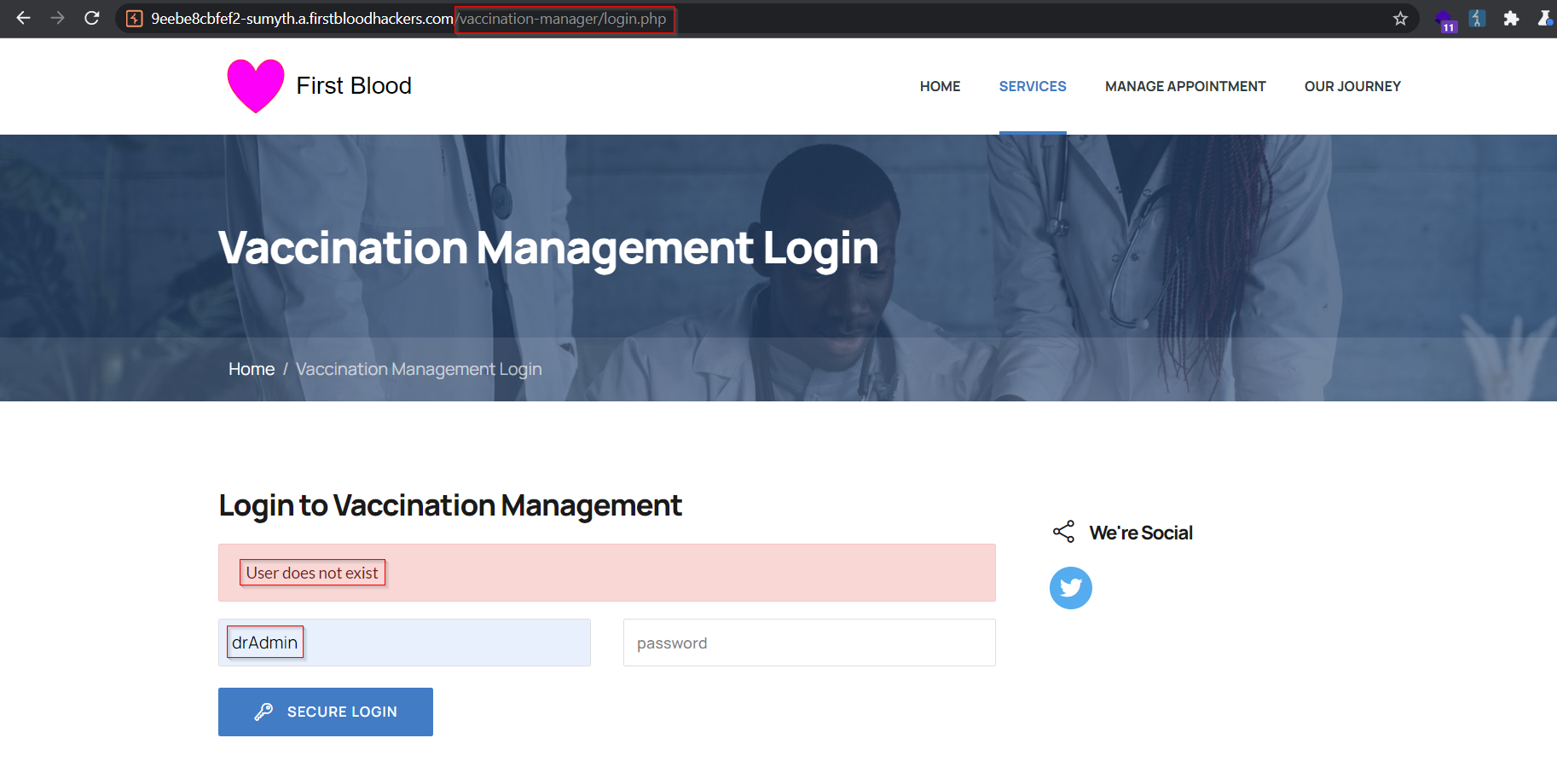
- It is observed that username 'admin' is a valid user of vaccine management portal as shown in the response from server,
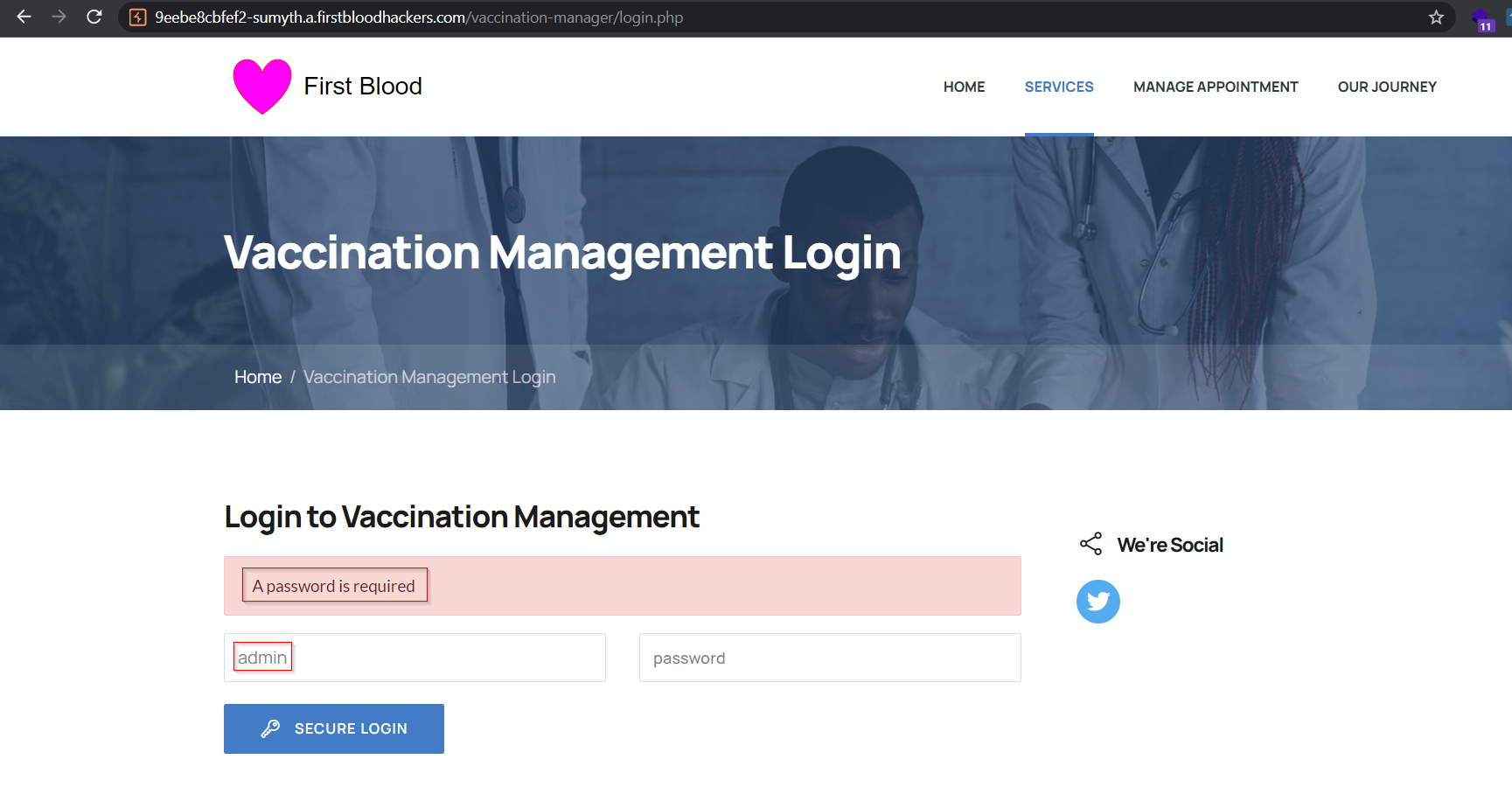
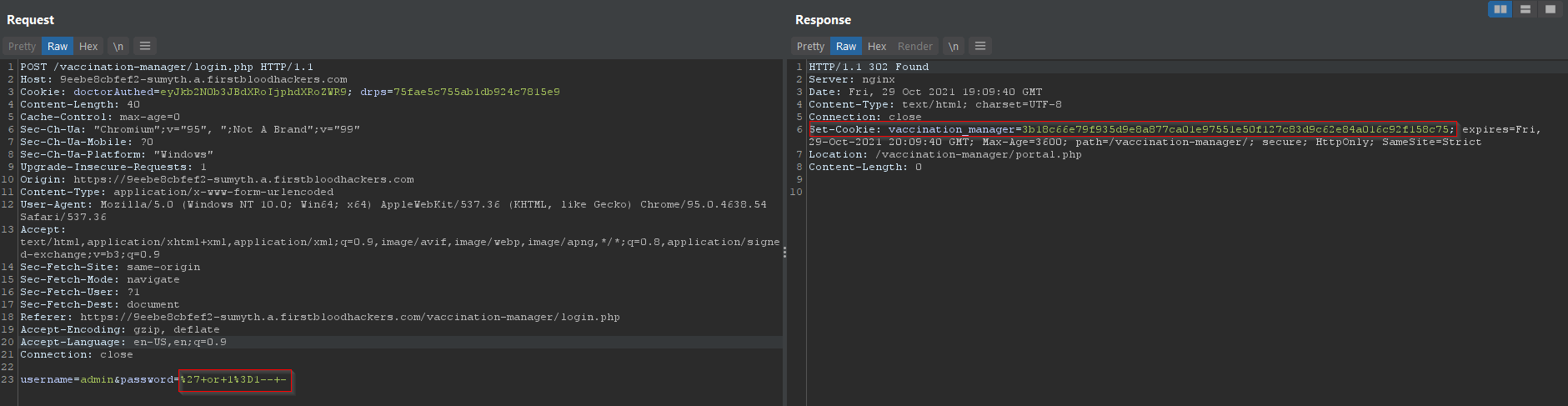
- The password field on this page is also vulnerable to SQLi attacks. Using a simple payload to bypass the authentication -
%27+or+1%3D1--+-, we are able to login to the portal.
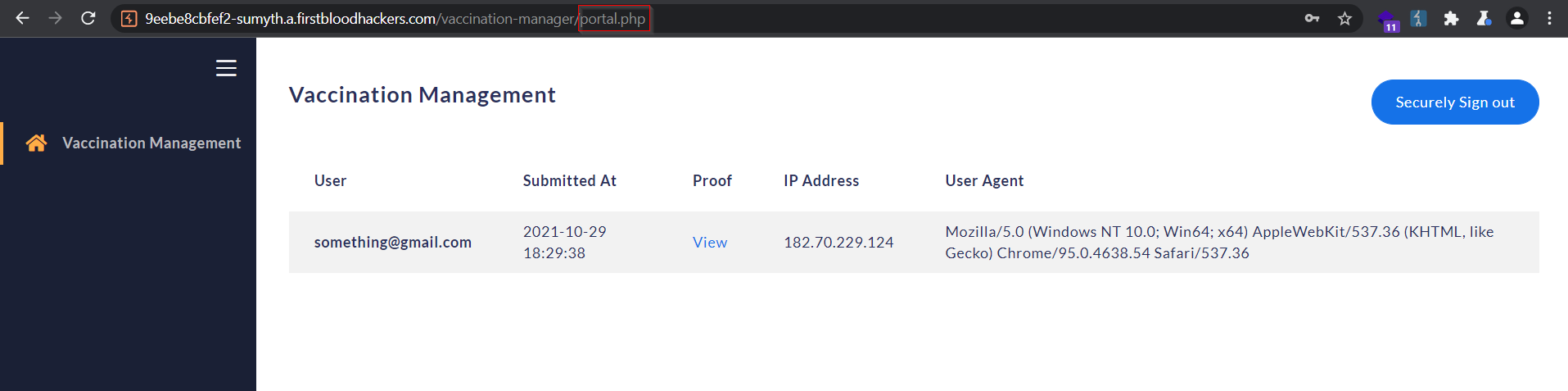
The portal also allows to view the vaccination certificates directly leading to direct disclosure of sensitive PII.
Impact
Username enumeration along with SQL Injection in login page will allow an attacker to easily bypass the login restrictions and gain access to sensitive PII.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Parameter:
Payload:
FirstBlood ID: 30
Vulnerability Type: SQL Injection
There is an SQL injection on the vaccination management portal login page which results in the user being able to login as the administrator.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


