FirstBlood-#875 — SQL Injection in vaccine management login can be used to view appointment details table
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-29, sumyth Level 2 reported:
Hi,
Please find a brief description of the vulnerability below,
Summary
Using the SQLi identified in FirstBlood-#873, it is possible to fully enumerate the backend database and view sensitive information stored in appointments table.
Steps to Reproduce:
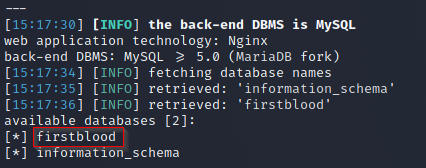
- Utilize the SQLi identified in FirstBlood-#873 and launch SQLMap. It is observed that database 'firstblood' has a table named 'appointments'.
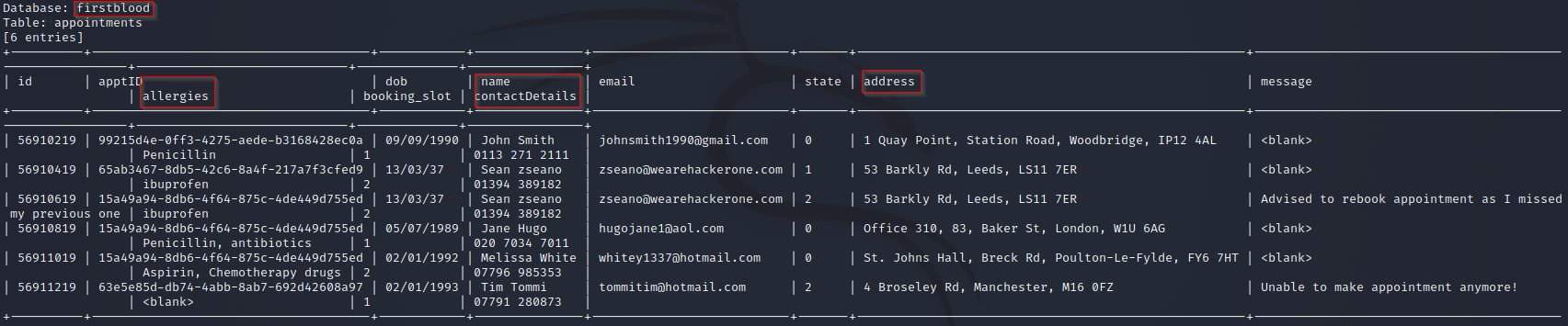
- The appointments table can be further dumped to reveal sensitive details with regards to appoints made by patients. The information include allergies, contact details, addresses etc.
The disclosed appointment IDs can also be utilized to modify appointments by any user as well.
Impact
Using SQLi, an attacker can gain access to the extremely sensitive PII data of patients and also modify their appoints using appointment IDs disclosed.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /vaccination-manager/login.php
Parameter: password
Payload: NA
FirstBlood ID: 30
Vulnerability Type: SQL Injection
There is an SQL injection on the vaccination management portal login page which results in the user being able to login as the administrator.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
