Dear FirstBlood security team, I found a vulnerability on your service.
I hope this report will help you.
This bug is found with my collaboration partner mrroot, huge thanks to him
Summary
Since Login to Vaccination Management page is vulnerable to SQL injeciton, the malicious user can log in without authentication.
Vulnerability Description(PoC)
This bug is composed of some flaws in login page.
First of all, if we enter a random username like hoge and password like aaa, then User does not exist notification appears.
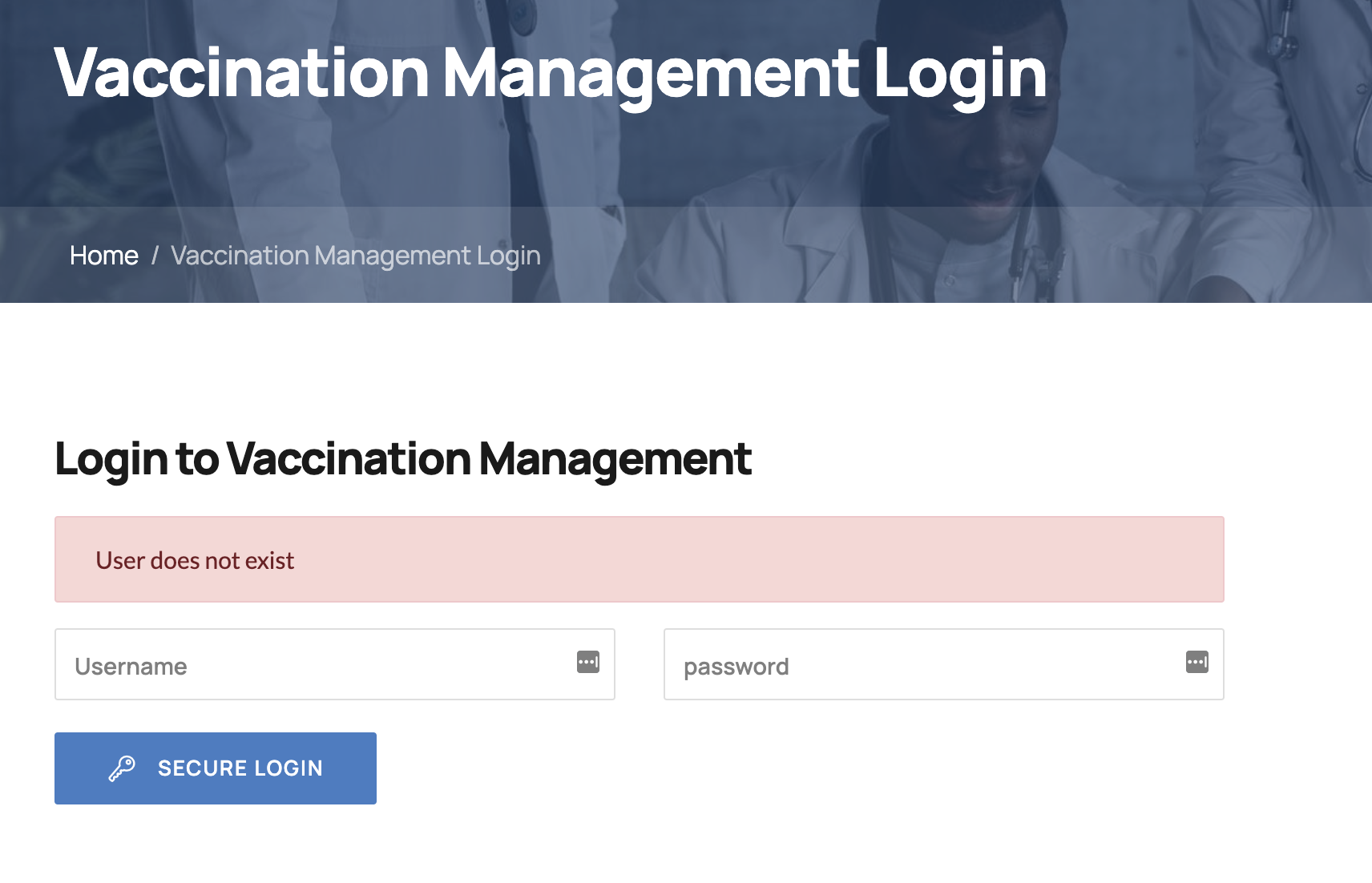
mrroot discovered that that notification's message is changed to Invalid username or password if we enter username's value as admin.
This implies that there is admin account and only password is wrong.

Next, we tried to guess password but failed.
Finally, I discovered password param is vulnerable to SQL injection like password=aaa' or 1=1#.
Note: this SQL injection appears only when we input a valid username like admin.
If all things are correct, we can log in without any authentication as admin account.

Impact
- the attacker can bypass authentication and log in as a valid user
- not only authentication bypass, but also the attacker can extract information from DB by using UNION-base SQL injection
This screenshot shows that we can get the information like there is no table named user in firstblood database.
We didn't test more but it's highly possible to apply Time-based SQL injection to extract entire data from DB.

Regards,
kinako and mrroot
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


