Summary:
Hi
In my previous report, I and @Ayush1098 found out that it was possible to change profile photo of other doctors using the photoUrl parameter. However, I noticed that the // gets replaced by a /. So by providing a /// we can link images from external hosts as the profile photo of other doctors.
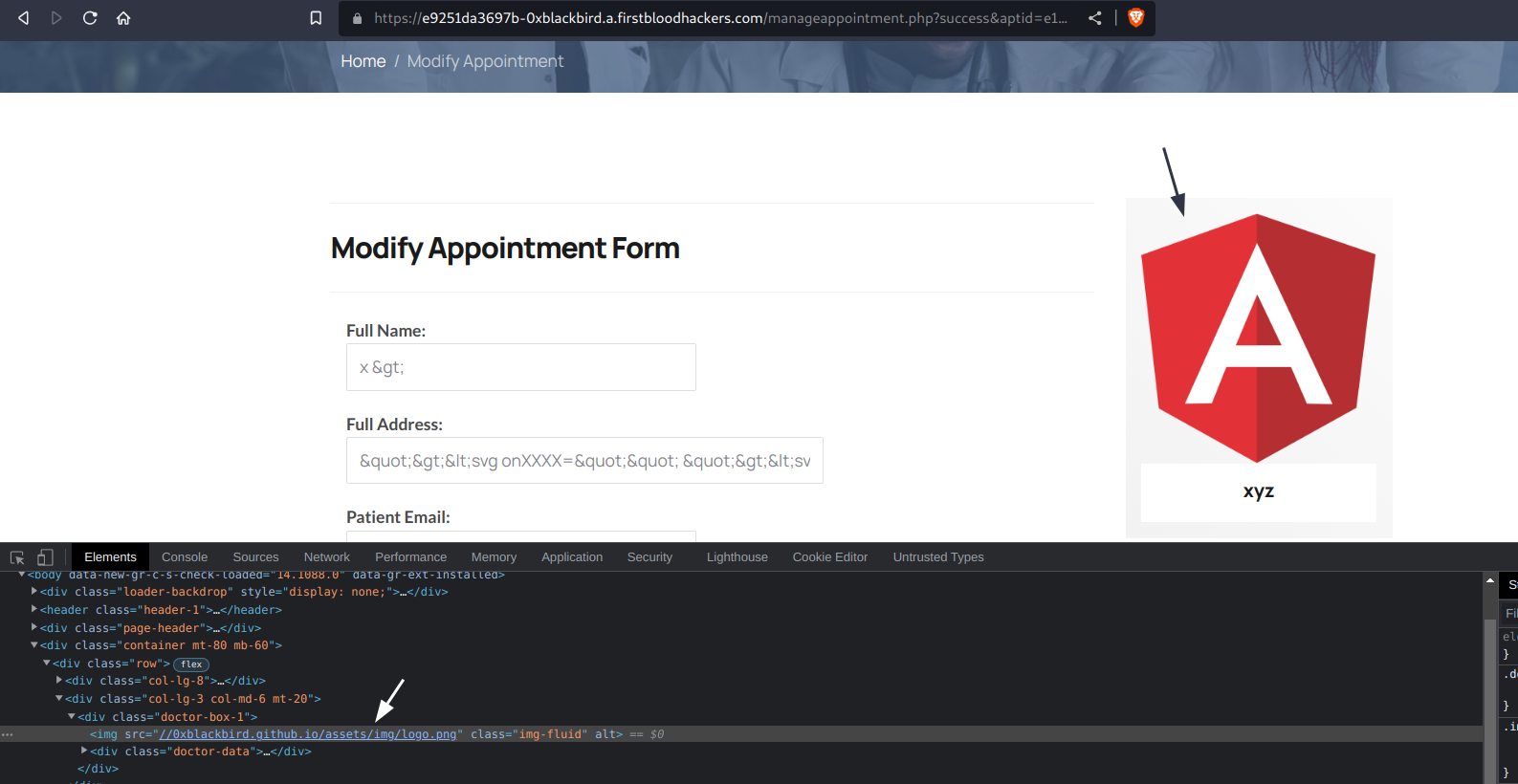
I'm unsure if this should be reported in a separate report or just be included in my previous report. That's why I decided to report it in as a new submission.
Possible cause:
The developers thought replacing a // with a / was sufficient to mitigate this, however, this is not the case as it doesn't look for it recursively
Impact:
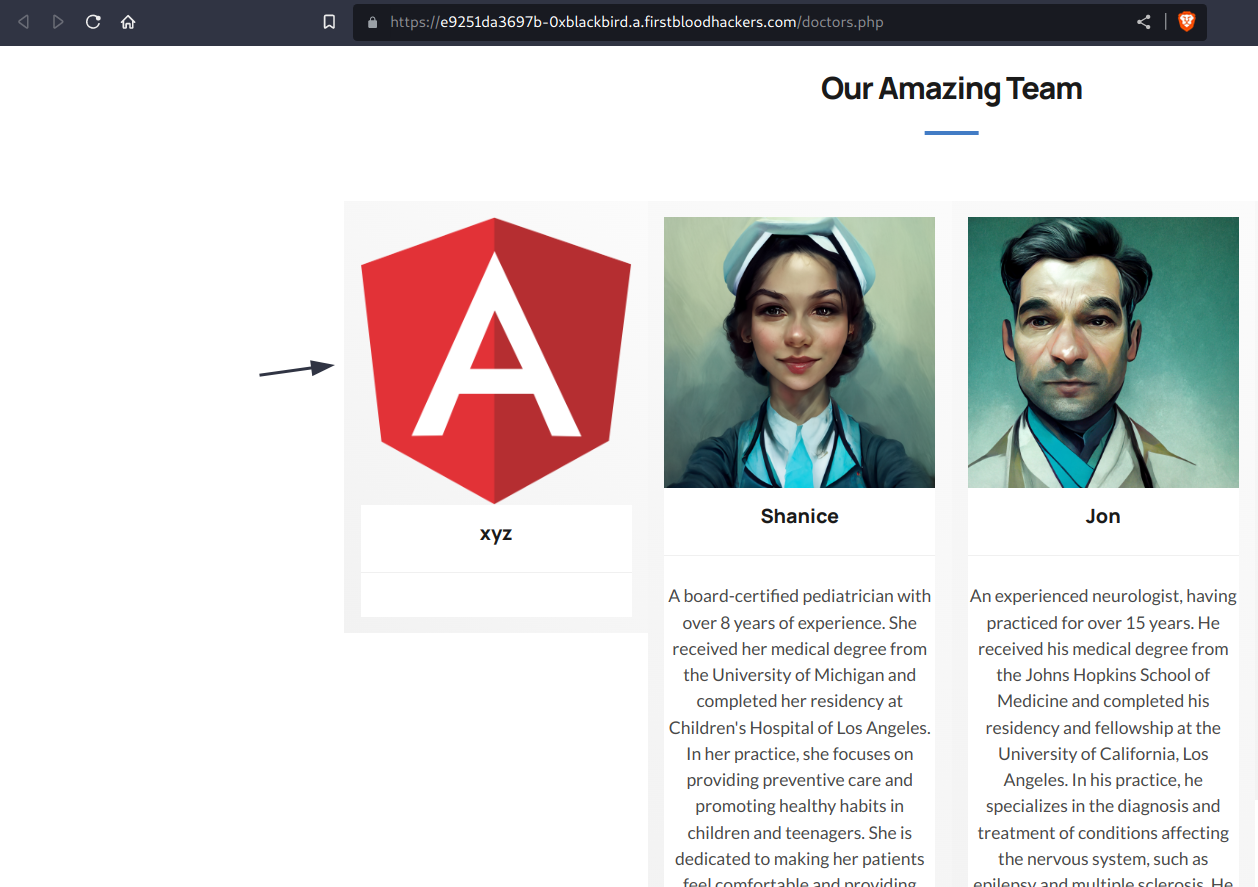
I'm no more only able to link resources on firstblood but also it load from external resources. This can cause reputable damage to doctors if their photo gets changed to something unapproperiate.
Steps to reproduce:
1) Login using the default credentials: admin:admin
2) Next, replicate the following request:
POST /drpanel/drapi/edit-dr.php HTTP/1.1
Host: {HOST}
Cookie: drps={SESS_COOKIE}
Content-Type: application/x-www-form-urlencoded
Content-Length: 85
drid=1&name=xyz&bio=&bookable=0&photoUrl=///{HOST}/{PATH_TO_IMG}.png
3) Once sent, we can visit /doctors.php or /manageappointment.php?success&aptid={ID} to double check this:
Mitigation:
I recommend removing the photoUrl parameter from the API endpoint.
If you have any additional questions regarding this submission. Please do not hesitate to ask.
Kind regards,
0xblackbird
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

 Report Feedback
Report Feedback