FirstBlood-#1804 — Appointment UUIDs leaked through new ambulances API endpoint
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-17, 0xblackbird Level 5
reported:
Summary:
Hi
I found out that the /api/ambulances.php discloses UUIDs + private data of all appointments made (where ambulance was set to 1 during booking). This should not be possible for unprivileged users.
Possible cause:
The developers may have added the all keyword for debugging purposes but forgot about it somehow.
Impact:
I was able to reveal the all the private appointment's data + UUID (this allows me to modify them for example). This shouldn't be possible.
Steps to reproduce:
1) After visiting /api/ambulances.php?select=all for example, we can find the full location in the response
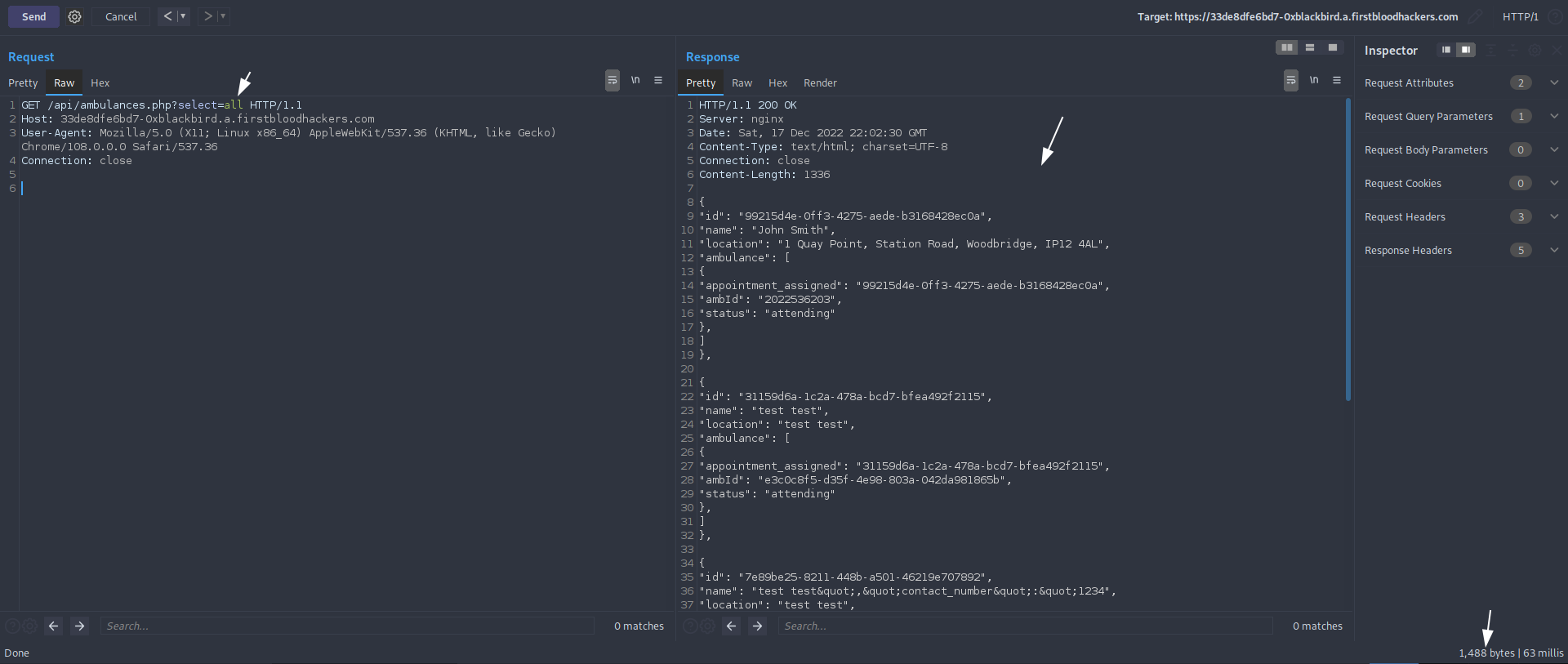
Mitigation
I recommend removing all keyword from this endpoint for unprivileged users.
Have a nice day!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/ambulances.php
Parameter: select
Payload: all
FirstBlood ID: 71
Vulnerability Type: Information leak/disclosure
The endpoint /api/ambulances.php leaks patient information if the parameter ?select=all is supplied
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 