FirstBlood-#607 — DOM-based XSS on /login.php via the goto parameter
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, 0xblackbird Level 5
reported:
Hello! The DOM XSS that I reported a while ago is still unpatched. This issue can still be exploited by crafting a payload and appending it to the url. This can lead to account takeover of course.
Proof of concept:
Steps to reproduce:
-
The goto parameter is here to redirect the doctors after they've logged in successfully, and since this redirection happens on the client-side (via JavaScript), we can use the javascript protocol to execute javascript. To do so, we first have to have valid credentials. In one of my previous reports, I've discovered that test credentials could be used (or you can just reset someone else's password by making a POST request to the following endpoint: /drpanel/drapi/editpassword.php. More info in my previous report).
-
Visit the proof of concept URL and use the following test credentials: testdoctor:test. Click on "SECURE LOGIN".
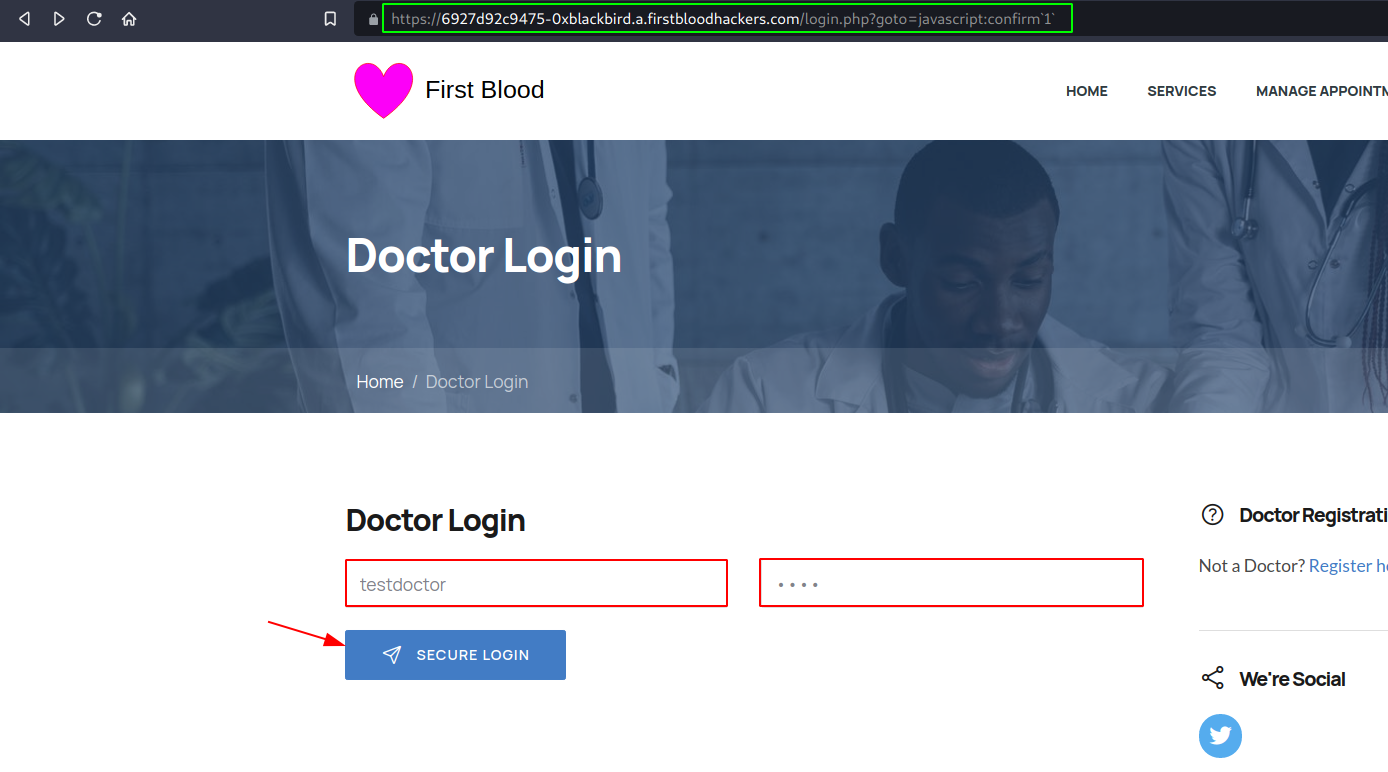
- And normally the confirm box should pop-up:
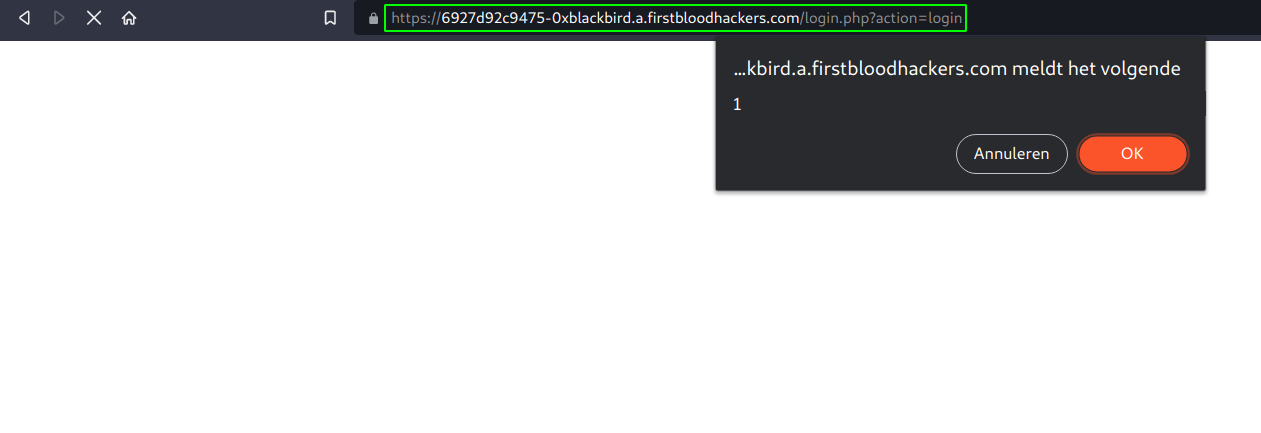
- The issue here (viewable from the blank page after redirection):
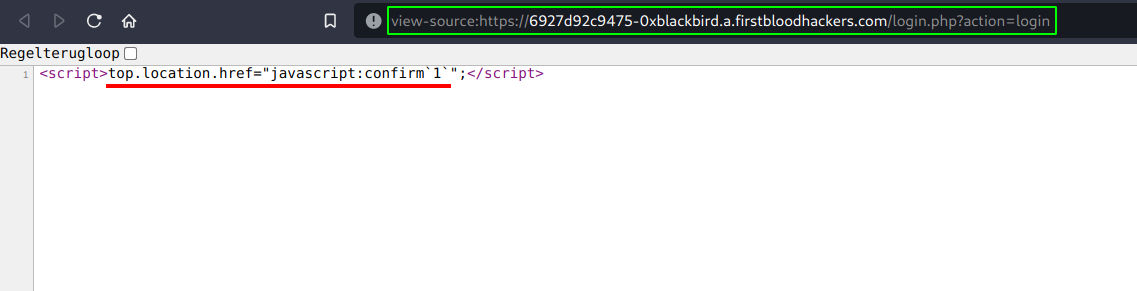
Escalation:
Of course a bad actor would not just go for a confirm box and stop. That's why I decided to prove the impact of this bug. In the following proof of concept, I'm going to demonstrate that it's easy for an attacker to send his/her victim a special crafted link and after that the victim has logged in, send the cookies to the attacker's end. There are a few possible ways to do so, one way is to just redirect the victim to your server with the session cookie(s) appended as the value of a GET parameter for example.
- First of all, visit the other proof of concept URL (to proof the account takeover, make sure you adjust the URL in the PoC). And repeat the previous steps (entering the test credentials).
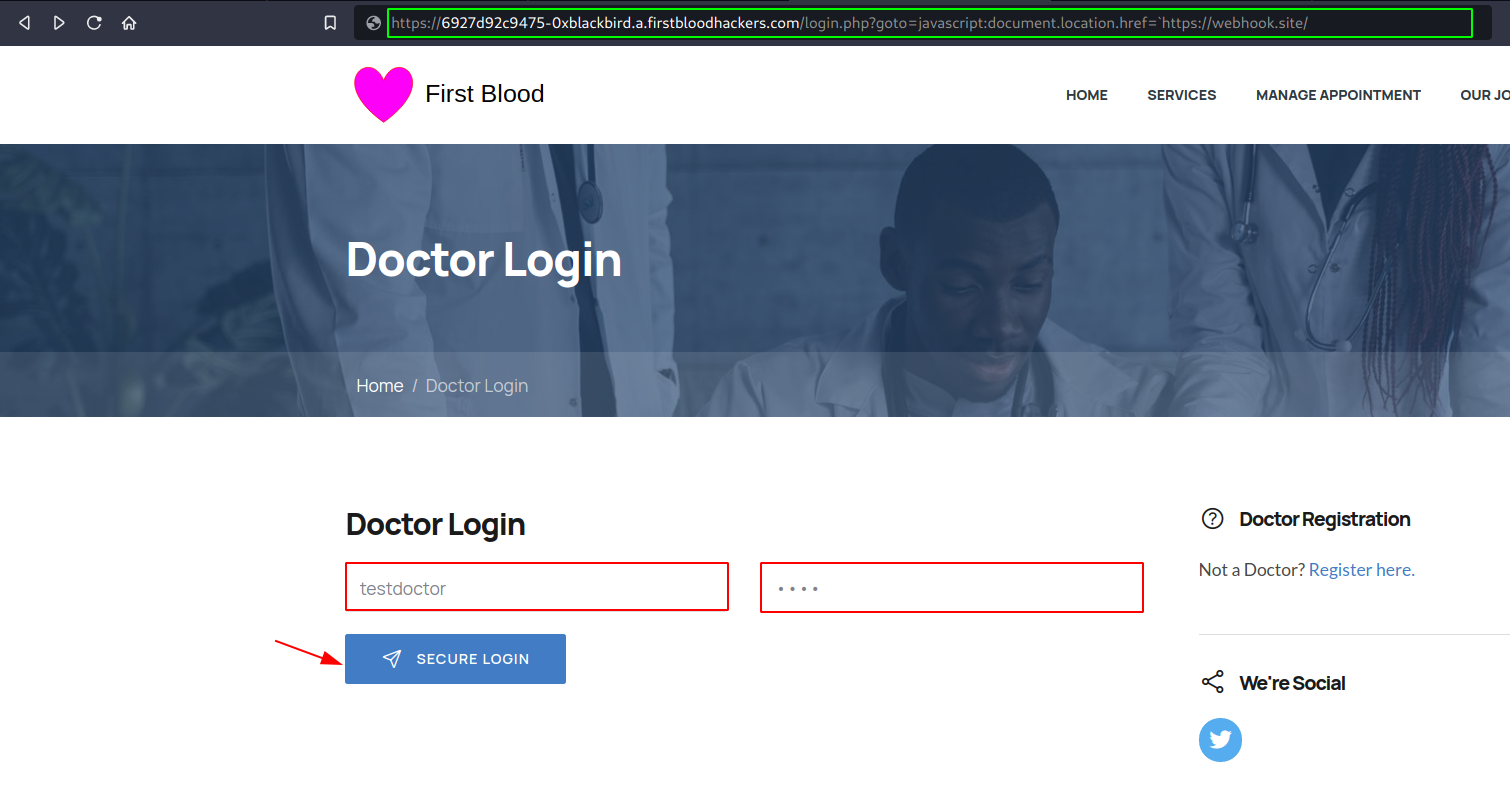
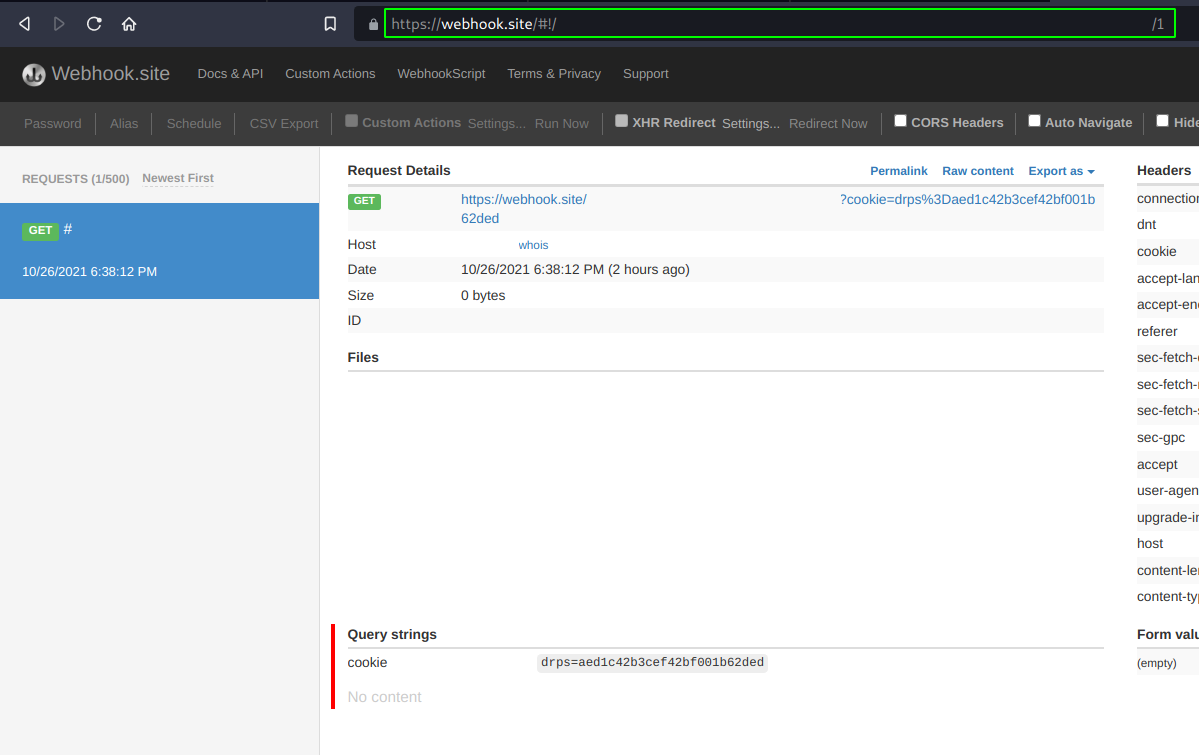
- Next, click on "SECURE LOGIN". I used webhook.site to view the parameters (since I don't have a server available for the moment), you can of course also setup a local server just for demo purposes. And after logging in, you should see the cookies in your URL bar as well as a the request coming in on your side with the cookies.
Thanks! Have a nice day!
Kind regards,
0xblackbird
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login.php
Parameter: goto
Payload: javascript:confirm`1`
FirstBlood ID: 39
Vulnerability Type: Reflective XSS
Our mistake: The parameter "goto" on login.php should of been "fixed" when redirecting to prevent XSS but due to an oversight from Sean and Karl, the new code did not make it into production. This has since updated since the event ended and you're recommended to re-try. It's related to bug ID 26 because the idea was developers fixed *this* one (when redirecting) but forgot the other reflection.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




